You have a Microsoft 365 subscription that includes 500 Windows 10 Enterprise 22H2 devices that are managed by using Microsoft Intune. You plan to update the devices to Windows 11. You need to identify the devices that do NOT meet the requirements for Windows 11. What report should you review?
All devices report
Device Compliance report
Windows feature update device compatibility risks report
Windows feature update device readiness report
The Windows feature update device readiness report in Intune provides detailed information about which devices are ready for a specific Windows feature update, such as Windows 11. It highlights devices that do not meet the requirements, helping you quickly identify and address compatibility issues before deployment.
You have a Microsoft 365 subscription that includes 500 Windows 10 Enterprise 22H2 devices that are managed by using Microsoft Intune. You need to update the devices to Windows 11. The solution must ensure that users can postpone the update for a maximum of two weeks. What should you configure first?
Device configuration profile
Feature update policy
Quality update profile
Update ring policy
An update ring policy in Intune allows you to control how and when updates are delivered to Windows devices, including setting deadlines and deferral periods for feature updates. By configuring an update ring policy, you can specify that users are allowed to postpone the Windows 11 update for up to two weeks, ensuring compliance with your organization’s update schedule while providing flexibility for users.
You have a Microsoft 365 subscription that includes 50 corporate iOS devices that are enrolled in Microsoft Intune. You need to ensure that iOS updates are deferred for 90 days. The solution must prevent users manually installing updates during the 90-day period. What should you configure?
Compliance policy
Configuration profile
Update policy
Update Ring profile
To defer iOS updates and prevent users from manually installing updates during the deferral period, you should configure a device configuration profile in Intune. This profile allows you to set update deferral settings and restrict user actions related to updates on iOS devices, ensuring compliance with your organization’s update management policy. Update rings are used for Windows, not iOS.
You have a Microsoft 365 subscription that includes the following devices: Device1: Windows 10 Pro version 22H2 Device2: Windows 11 Pro version 23H2 Device3: Windows 11 Home version 23H2 Device4: Windows 11 Enterprise version 22H2 You need to manage updates for the Windows devices by using update rings in Microsoft Intune. Which devices can be managed by using Microsoft Intune?
Device3 and Device4 only
Device2, Device3, and Device4 only
Device1, Device2, and Device4 only
Device4 only
Microsoft Intune update rings can only manage Windows 10/11 Pro, Enterprise, and Education editions. Windows Home edition (Device3) is not supported for update ring management in Intune. Therefore, only Device1 (Windows 10 Pro), Device2 (Windows 11 Pro), and Device4 (Windows 11 Enterprise) can be managed.
You have a Microsoft 365 E5 subscription that contains devices that run Windows 11. All the devices are enrolled in Microsoft Intune. You need to ensure that the devices use Delivery Optimization when installing Windows updates. What should you configure in Intune?
device configuration profile
feature updates for Windows 10 and later
quality updates for Windows 10 and later
update ring for Windows 10 and later
To configure Delivery Optimization settings for Windows updates, you must use a device configuration profile in Intune. This profile allows you to set policies that control how devices download updates, including enabling Delivery Optimization, which helps reduce bandwidth usage by allowing devices to share update files with each other. Update rings and update policies control the timing and type of updates, but not Delivery Optimization settings.
You have a Microsoft 365 subscription and 50 iOS devices. You plan to implement Defender for Endpoint for all corporate iOS devices. You need to onboard the iOS devices to Defender for Endpoint. What tool should you use?
Group policy
JAMF Pro
local scripts
Microsoft Intune
Microsoft Intune is the recommended tool for onboarding and managing iOS devices in a Microsoft 365 environment. It allows you to deploy Defender for Endpoint to all corporate iOS devices centrally, ensuring consistent security policies and streamlined device management. Group Policy and local scripts are not applicable for iOS, and JAMF Pro is typically used for macOS management, not for Microsoft Defender for Endpoint integration in a Microsoft 365 environment.
You have a Microsoft 365 E5 subscription that includes 500 Windows 11 devices that are managed by using Microsoft Intune. You need to apply granular security controls to the Microsoft Edge configuration on each device. The solution must minimize administrative efforts. What should you configure?
a Compliance policy
a Security Baseline
Attack surface reduction
Endpoint detection and response
A Security Baseline in Intune provides a pre-configured set of recommended security settings, including granular controls for Microsoft Edge. Applying a security baseline ensures consistent and comprehensive security configurations across all devices with minimal administrative effort, as the baseline is maintained and updated by Microsoft.
You have a Microsoft 365 E5 subscription that uses Microsoft Intune. The following devices have Microsoft 365 apps installed and are enrolled in Intune: Device1: Windows 11 Device2: Android Device3: iOS You plan to use a Microsoft 365 Apps for enterprise security baseline named Baseline1. To which devices can you apply Baseline1?
Device1 and Device2 only
Device1 and Device3 only
Device1, Device2 and Device3
Device1 only
Microsoft 365 Apps for enterprise security baselines in Intune are only supported on Windows devices. You cannot apply these baselines to Android or iOS devices, so Baseline1 can only be applied to Device1 (Windows 11).
You have a Microsoft 365 subscription. You need to ensure that any Intune managed Windows 10 Device that has been inactive for 180 days is automatically wiped and that the enrollment is deleted from Microsoft Intune. What should you configure?
Compliance policies
Configuration profiles
Device Cleanup rules
Security Baselines
Device Cleanup rules in Intune allow you to automatically remove devices that have been inactive for a specified period (such as 180 days). This helps keep your device inventory up to date by deleting old, unused device records and can also trigger actions like device wipe, ensuring that inactive devices are securely removed from management.
You have a Microsoft 365 E5 subscription that uses Microsoft Intune. You have the following devices enrolled in Intune: Device1: Windows 11 Device2: macOS Device3: iPadOS You plan to use a template to create an Endpoint Protection device configuration profile in Intune. For which devices can you create an Endpoint Protection device configuration profile template?
Device1 and Device2 only
Device1 and Device3 only
Device1, Device2, and Device3
Device1 only
Endpoint Protection device configuration profile templates in Intune are available for Windows and macOS devices, but not for iPadOS. This means you can create and assign these profiles to Device1 (Windows 11) and Device2 (macOS), but not to Device3 (iPadOS).
You are building a Windows Autopilot solution. During testing you notice that deployments are failing due to users restarting devices before the deployment has finished. You need to provide users with the option of collecting logs during deployment and contact details for the help. What should you modify?
configuration policy
deployment profile
device group settings
Enrollment status page
The Enrollment status page (ESP) in Windows Autopilot allows you to control the user experience during device setup, including blocking restarts until deployment is complete, collecting logs, and displaying IT contact information. Modifying the ESP ensures users have the necessary support and prevents premature restarts that can cause deployment failures.
You have a Microsoft 365 E3 subscription that includes 500 devices and uses Microsoft Intune. The devices run Windows 10 22H2 and are configured with Windows Recovery Environment. You need to deploy Windows Autopilot. The solution must minimize the time taken to revert devices to a business-ready state. What should you do first?
Create a deployment profile.
Create a dynamic device group.
Enable the DisableAutomaticReDeploymentCredentials policy.
Manually register the devices with Windows Autopilot.
Creating a deployment profile is the first step in configuring Windows Autopilot. The deployment profile defines how devices are configured and provisioned during the Autopilot process, enabling quick and automated setup to a business-ready state. This minimizes manual intervention and speeds up the process of reverting devices for reuse or redeployment.
You plan to deploy 25 new Windows 11 devices that will be used by customers to browse the internet in a public location. You need to recommend a Windows Autopilot mode for the deployment. What should you recommend?
Windows Autopilot for existing devices
Windows Autopilot Reset
Windows Autopilot self-deploying mode
Windows Autopilot user-driven mode
Windows Autopilot self-deploying mode is designed for scenarios where devices are set up for shared or kiosk use, such as in public locations. This mode allows devices to be deployed with minimal user interaction, making it ideal for customer-facing or public-use devices where no user-specific setup is required.
You have a Microsoft 365 subscription. You purchase 100 Windows devices that will be deployed to new users. You need to ensure that you can deploy the devices by manually registering the devices using Windows Autopilot. What should you do first?
Upload the device name of each device to Microsoft Intune.
Upload the hardware ID of each device to Microsoft Intune.
Upload the IP address of each device to Microsoft Intune.
Upload the MAC address of each device to Microsoft Intune.
To register devices with Windows Autopilot, you must first upload the hardware ID (also known as the device hash) of each device to Microsoft Intune. This allows Autopilot to recognize and manage the devices during deployment. Device name, IP address, or MAC address are not sufficient for Autopilot registration.
You have a Microsoft 365 E5 subscription that contains a Microsoft Entra tenant. The tenant contains the following devices: Device1: Microsoft Entra joined Windows 11 device Device2: Microsoft Entra registered Windows 11 device Device3: Microsoft Entra joined Windows 10 device Device4: Microsoft Entra registered iOS device Which devices can be activated by using subscription activation?
Device1 and Device2 only
Device1 and Device3 only
Device1 only
Device1, Device2, and Device3 only
Device1, Device2, Device3, and Device4
Subscription activation is supported for Windows 10 and Windows 11 devices that are either Microsoft Entra joined or Microsoft Entra registered. It is not supported for iOS devices. Therefore, only Device1, Device2, and Device3 can be activated using subscription activation.
Your company has a mix of corporate-owned and BYOD (Bring Your Own Device) devices used by employees to access company data. The IT department wants to ensure that corporate data is protected on both managed and unmanaged devices without affecting personal data. How should you implement a solution that protects corporate data at the app level while allowing employees to use their devices for personal tasks?
Deploy a VPN solution to secure all device communications.
Implement Intune App Protection Policies (APP) for both managed and unmanaged devices.
Require all devices to be enrolled in Intune MDM.
Use Microsoft Defender for Endpoint to monitor all devices.
Intune App Protection Policies (APP) allow you to protect corporate data at the application level, regardless of whether the device is managed or unmanaged. This means you can secure company data within specific apps (like Microsoft 365 apps) without requiring full device management, ensuring personal data and apps remain unaffected. This is ideal for BYOD scenarios where users use their own devices for both work and personal tasks.
You have a Microsoft 365 subscription that includes iOS and Android devices that are managed by using Microsoft Intune. You need to prevent users printing Microsoft Word documents stored in Microsoft 365 from their mobile devices by using an app protection policy. Which settings should you configure?
Access requirements
Conditional Access Policies
Conditional launch
Data Protection
The “Data Protection” settings in an Intune app protection policy allow you to control actions such as saving, copying, and printing corporate data from managed apps. To prevent users from printing Microsoft Word documents from their mobile devices, you would configure the relevant restrictions under Data Protection. This ensures sensitive information cannot be printed or shared outside of managed applications.
You have a Microsoft 365 subscription that uses Microsoft Intune. You plan to implement a bring your own device (BYOD) policy to support iOS and Android devices. You need to ensure that users can access all Microsoft 365 Apps on their devices. The solution must meet the following requirements: Prevent users copying and pasting information from Microsoft 365 apps to non-Microsoft apps. Private devices must not be enrolled to Microsoft Intune. What should you configure?
a Conditional Access policy
a Device Restriction policy
an App Protection policy
an App Configuration policy
An App Protection policy allows you to protect corporate data at the app level, even on devices that are not enrolled in Intune. With this policy, you can restrict actions like copying and pasting data from Microsoft 365 apps to personal apps, which is ideal for BYOD scenarios where you do not want to require full device enrollment. This ensures data security while supporting user privacy on personal devices.
You have a Microsoft 365 subscription that includes a group named Group1 that contains 500 Android devices. You provision a new App Protection policy in Microsoft Intune with the following settings: Target to apps on all device types: Yes Target Policy to: All Microsoft Apps Save copies of org data: Block Allow user to save copies to selected services: OneDrive for Business Assignments: Group1 Users report that they can save data to their devices. You need to ensure that users are prevented from saving data to their local devices. Which setting should you modify?
Allow user to save copies to selected services
Assignments
Save copies of org data
Target Policy to
The setting “Allow user to save copies to selected services” currently allows users to save data to OneDrive for Business, which may also permit saving to local devices depending on how the app handles file storage. To fully prevent users from saving data to their local devices, you should modify this setting to remove all selected services, ensuring that saving is completely blocked and data cannot be stored locally. This enforces stricter data protection and prevents data leakage.
You have a Microsoft 365 subscription that includes 100 users. Users access Microsoft 365 services by using Microsoft Edge on personal Android devices. You need to deploy Microsoft Edge bookmarks to the Android devices. What should you configure?
a Compliance policy
a Configuration profile
an App Configuration policy
an App Protection policy
An App Configuration policy in Intune allows you to configure and deploy specific app settings, such as bookmarks, to managed apps like Microsoft Edge on Android devices. This is the recommended way to centrally manage and push configuration settings to apps, even on personal (BYOD) devices. Compliance policies and protection policies do not configure app-specific settings, and configuration profiles are used for device settings, not app settings.
You have a Microsoft 365 E5 subscription that uses Microsoft Intune. You have the following devices: Device1: Windows 11 device enrolled in Intune Device2: Android device enrolled in Intune Device3: Android device NOT enrolled in Intune Device4: iOS device NOT enrolled in Intune To which devices can you apply an app configuration policy?
Device1 and Device2 only
Device1, Device2, Device3 and Device4
Device1 only
Device2, Device3 and Device4 only
Device3 and Device4 only
App configuration policies in Intune can be applied to both enrolled and unenrolled Android and iOS devices (using app protection and configuration policies for managed apps). However, they cannot be applied to Windows devices. Therefore, you can apply an app configuration policy to Device2 (enrolled Android), Device3 (unenrolled Android), and Device4 (unenrolled iOS).
You have a Microsoft 365 E5 subscription that uses Microsoft Intune. You have the following devices enrolled in Intune: Device1: Windows 11 Device2: Android Device3: iOS You plan to create an app configuration policy named Config1 in Intune. To which devices can you apply Config1?
Device1 and Device2 only
Device1 and Device3 only
Device1, Device2 and Device3
Device2 and Device3 only
App configuration policies in Intune are designed for mobile platforms, specifically Android and iOS devices, to manage app settings and configurations. These policies cannot be applied to Windows devices, so Config1 can only be applied to Device2 (Android) and Device3 (iOS).
Your company has recently migrated to Microsoft Intune to manage their endpoint devices. They have a mix of Windows 10 and Windows 11 devices and need to deploy a critical line-of-business (LOB) application packaged as a Win32 app. The application must be installed on all devices in the Sales department. How should you ensure that the application is deployed and kept up to date automatically?
Deploy the application using Group Policy and assign it to the Sales department OU.
Manually install the application on each device and configure Windows Update to keep it updated.
Use the Intune Management Extension to deploy the Win32 app and configure it as a required app for the Sales department group.
Use the Microsoft Store for Business to deploy the application and assign it to the Sales department group.
The Intune Management Extension allows you to deploy and manage Win32 apps on both Windows 10 and Windows 11 devices. By configuring the app as “required” for the Sales department group, Intune will automatically install and keep the app up to date on all targeted devices, ensuring compliance and reducing manual effort. This is the recommended and most efficient method for deploying and maintaining Win32 line-of-business apps in a modern managed environment.
Your company is planning to deploy Windows Hello for Business in a hybrid environment using both on-premises Active Directory and Microsoft Entra ID. They want to ensure a seamless deployment without conflicts between Group Policy and Intune settings. How should you configure the devices to implement Windows Hello for Business in this hybrid environment?
Configure Windows Hello for Business settings in both Intune and Group Policy without any coordination.
Disable Windows Hello for Business in Intune and use only on-premises AD DS settings.
Use Intune to manage Windows Hello for Business settings and ensure no overlapping settings with Group Policy.
Use only Group Policy to manage Windows Hello for Business settings.
To avoid conflicts and ensure a seamless deployment, you should use only one management tool (Intune or Group Policy) to configure Windows Hello for Business settings. If you choose Intune, make sure there are no overlapping or conflicting settings in Group Policy. This prevents policy conflicts and ensures consistent configuration across all devices in the hybrid environment.
Your company is planning to deploy Microsoft 365 Apps to their Windows 11 devices using Intune. They want to ensure that all previous MSI versions of Office are removed during the deployment to avoid conflicts. How should you configure the deployment to remove all existing MSI versions of Office from the devices?
Deploy the Microsoft 365 Apps as a Win32 app to handle the removal of MSI versions.
Enable the ‘Remove MSI from end-user devices’ option in the app suite configuration.
Manually uninstall all MSI versions of Office from each device before deploying Microsoft 365 Apps.
Use a PowerShell script to remove MSI versions of Office before deploying Microsoft 365 Apps.
When deploying Microsoft 365 Apps with Intune, you can enable the ‘Remove MSI from end-user devices’ option in the app suite configuration. This ensures that any existing MSI-based Office installations are automatically detected and removed during the deployment process, preventing conflicts and streamlining the upgrade to Microsoft 365 Apps. This is the recommended and most efficient method.
You have a Microsoft 365 E5 subscription that uses Microsoft Intune. All Android devices are enrolled in Intune. You need to add Android apps to Intune. For which app type should you first connect Intune to an Android Enterprise account?
Android Enterprise system app
Android store app
line-of-business app
Managed Google Play app
To add Managed Google Play apps in Intune, you must first connect Intune to an Android Enterprise account. This integration is required to manage and deploy Managed Google Play apps to Android devices.
You have a Microsoft 365 subscription that includes 500 Windows 11 Enterprise devices that are managed by using Microsoft Intune. You plan to deploy Microsoft 365 Apps to the devices by using Intune. You need to limit the diagnostic data that is sent to Microsoft for the Microsoft 365 Apps. What should you create?
a Microsoft 365 Apps for Windows 11 configuration
an App Configuration policy
an App Protection policy
an Office Apps policy
To limit the diagnostic data sent to Microsoft for Microsoft 365 Apps, you should create and configure an Office Apps policy in Intune.
You have a Microsoft 365 subscription that includes 500 Windows 11 Enterprise devices that are managed by using Microsoft Intune. You add an app named App1 to Microsoft Intune. You need to ensure that App1 is automatically installed for all users. What should you configure for App1?
App Configuration policies
App settings
Application assignments
Application information
To ensure an app is automatically installed for all users, you must configure the application assignments in Intune and set the app as “Required” for the target group.
You have a Microsoft 365 subscription that includes the following resources: A user named User1 Two groups named Group1 and Group2 A Windows 10 device named Device1 Device1 is a member of Group1. User1 is a member of Group2. You deploy a new Windows 10 app named App1 to User1 on Device1 with the following assignments: Required: Group1 Uninstall: Group2 When User1 signs into Device1, what is the status of App1 on the device?
The app will be installed and will be available in the Company Portal.
The app will be installed and will NOT be available in the Company Portal.
The app will be uninstalled and will be available in the Company Portal.
The app will be uninstalled and will NOT be available in the Company Portal.
Since Device1 is a member of Group1 (which has the app as Required), the app will be installed on Device1. Required apps are installed automatically and do not appear in the Company Portal for users to install manually. The uninstall assignment for Group2 does not apply to Device1, as it is not a member of Group2.
You have a Microsoft 365 subscription that includes 100 Android devices that are enrolled to Microsoft Intune. You plan to deploy an Android app to all managed Android devices by using Microsoft Intune. You create a new app deployment and enter the name and details of the app. What should you do next?
Enter the AppStore URL for the app.
Enter the publishers download URL for the app
Upload the APK for the app to Azure storage.
Upload the APK for the app to the Microsoft Intune admin center.
After entering the app details, you must upload the APK file directly to the Microsoft Intune admin center to deploy the app to managed Android devices.
You have a Microsoft 365 subscription that includes 100 Windows 10 devices that are enrolled to Microsoft Intune. You need to deploy Microsoft 365 Apps for Business to all devices. The solution must ensure that Microsoft Visio is included in the deployment. What should you do first?
Assign a Visio license to your admin account.
Create a device configuration from the Microsoft 365 Apps admin center.
Create a device configuration profile from the Microsoft Intune admin center.
Create a new app configuration policy from the Microsoft Intune admin center.
To ensure Microsoft Visio is included in the deployment, you should first create a device configuration from the Microsoft 365 Apps admin center, where you can customize the Office installation to include Visio.
You have a Microsoft 365 subscription that includes a Windows device named Device1 that is enrolled in Microsoft Intune. Device1 has the following configuration: OS Architecture: 64-bit Join Type: Microsoft Entra joined Enrollment Type: Intune enrolled You purchase a new app named App1 that has the following configuration: Architecture: 32-bit IntuneWin file size: 9GB You need to deploy App1 to Device1 by using Microsoft Intune. What should you do first?
Download a 64-bit version of the source files.
Enable Co-management.
Microsoft Entra Hybrid Join the device.
Reduce the file size of the IntuneWin file.
Microsoft Intune has a maximum IntuneWin file size limit of 8GB. Since the current file is 9GB, you must reduce the file size before deployment.
You have a Microsoft 365 subscription that uses Microsoft Intune. You create a Conditional Access Policy named Policy1. You need to configure Policy1 to prevent users connecting to Microsoft 365 services by using non-compliant devices. What should you configure in Policy1?
Authentication Context
Continuous Access Evaluation
Grant Controls
Session Controls
In a Conditional Access policy, you use Grant Controls to enforce requirements such as “Require device to be marked as compliant.” This ensures that only compliant devices can access Microsoft 365 services, blocking access from non-compliant devices and helping maintain your organization’s security standards.
You have a Microsoft 365 E5 subscription that contains 10 Android Enterprise devices. Each device has a corporate- owned work profile and is enrolled in Microsoft Intune. You need to configure the devices to run a single app in kiosk mode. Which Configuration settings should you modify in the device restrictions profile?
Users and Accounts
General
System security
Device experience
The correct answer is D. Device experience because this section of the Device restrictions profile in Microsoft Intune for Android Enterprise corporate-owned work profile devices includes the configuration for kiosk mode settings. Kiosk mode allows administrators to lock down a device to a single app or a set of apps, ensuring the device is used only for its intended purpose?such as a point-of-sale terminal, digital sign, or dedicated business tool. The Device experience category provides options to configure this behavior, including selecting the kiosk app and enforcing restrictions that prevent users from exiting the app. The other settings?Users and Accounts, General, and System security?manage user permissions, baseline restrictions, and security configurations but do not control kiosk mode behavior, making Device experience the correct and most relevant option.
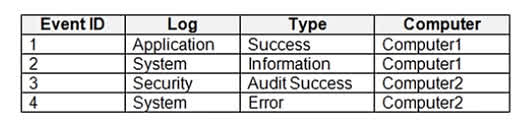
You have computers that run Windows 10 and connect to an Azure Log Analytics workspace. The workspace is configured to collect all available events from the Windows event logs. The computers have the logged events shown in the following table. Which events are collected in the Log Analytics workspace?
1 only
2 and 3 only
1 and 3 only
1, 2, and 4 only
1,2,3 and 4
The correct answer is D. 1, 2, and 4 only because the Azure Log Analytics workspace is configured to collect all available events from the Application and System logs by default, which includes events such as Success, Information, and Error types. However, Security logs, like Event 3 with type Audit Success, require additional configuration and permissions to be collected, which is not stated in the scenario. Therefore, only the events from the Application and System logs?Event IDs 1, 2, and 4?are collected by default, making D the correct choice.
You have a Microsoft 365 subscription that uses Microsoft Intune Suite. You use Microsoft Intune to manage devices. You need to review the startup times and restart frequencies of the devices. What should you use?
Azure Monitor
Intune Data Warehouse
Microsoft Defender for Endpoint
Endpoint analytics
The correct answer is D. Endpoint analytics because it is specifically designed to provide insights into device performance and user experience, including metrics such as startup times, restart frequencies, and application reliability. Endpoint analytics is part of Microsoft Intune and is integrated into the Microsoft Endpoint Manager admin center. It helps IT administrators proactively identify and remediate performance issues across managed Windows devices. Unlike Azure Monitor (which focuses on infrastructure and application telemetry), Intune Data Warehouse (which is used for custom reporting and historical data analysis), or Microsoft Defender for Endpoint (which focuses on security and threat protection), Endpoint analytics is tailored to optimize end-user productivity and device health, making it the right tool for reviewing startup and restart metrics.
You have a Microsoft 365 subscription that uses Microsoft Intune Suite. You use Microsoft Intune to manage devices. You have a Windows 11 device named Device1 that is enrolled in Intune. Device1 has been offline for 30 days. You need to remove Device1 from Intune immediately. The solution must ensure that if the device checks in again, any apps and data provisioned by Intune are removed. User-installed apps, personal data, and OEM-installed apps must be retained. What should you use?
a Delete action
a Retire action
a Fresh Start action
an Autopilot Reset action
The correct answer is A. a Delete action because the goal is to immediately remove Device1 from Intune, even though the device has been offline for 30 days. The Delete action in Microsoft Intune removes the device record from Intune and flags it for removal. When the device next checks in, Intune will recognize that it was deleted and will automatically unenroll it, triggering the removal of all Intune-managed apps, settings, and data. Importantly, this action does not wipe user-installed apps, personal files, or OEM preinstalled software, which meets the requirement of retaining those elements. In contrast, the Retire action waits for the device to check in and cannot be initiated immediately for offline devices. Fresh Start and Autopilot Reset are used for resetting the OS and user state, which would remove personal data?therefore, they do not meet the requirement.
You have a Microsoft 365 subscription. You have 10 computers that run Windows 10 and are enrolled in mobile device management (MDM). You need to deploy the Microsoft 365 Apps for enterprise suite to all the computers. What should you do?
From the Microsoft Intune admin center, create a Windows 10 device profile.
From Azure AD, add an app registration.
From Azure AD, add an enterprise application.
From the Microsoft Intune admin center, add an app.
The correct answer is D. From the Microsoft Intune admin center, add an app because deploying Microsoft 365 Apps for enterprise to managed Windows 10 devices is done by adding the suite as an app deployment within Intune. Since the devices are already enrolled in MDM, Intune can push applications directly to them. The admin can go to the Apps section in the Microsoft Intune admin center, choose to add an app, select Microsoft 365 Apps for Windows 10, and configure the deployment settings to install the suite on all targeted devices. This method ensures automated and centralized installation across all enrolled computers.
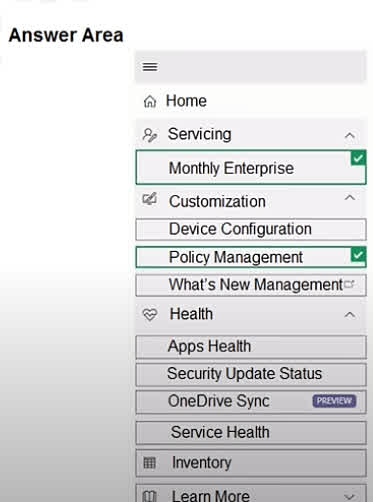
All users have Microsoft 365 apps deployed. You need to configure Microsoft 365 apps to meet the following requirements: Enable the automatic installation of WebView2 Runtime. Prevent users from submitting feedback. Which two settings should you configure in the Microsoft 365 Apps admin center? To answer, select the appropriate settings in the answer area. NOTE: Each correct selection is worth one point.
To view the answer, click ” Show Explanation “
The correct settings to configure in the Microsoft 365 Apps admin center are Device Configuration and Policy Management because these sections allow administrators to centrally manage app behavior and deployment settings. Device Configuration is used to control the installation behavior of Microsoft 365 apps, including enabling the automatic installation of WebView2 Runtime, which is required for certain modern app features. Policy Management, on the other hand, is used to enforce user-specific settings such as disabling feedback submission, ensuring users cannot send feedback to Microsoft. Together, these two settings meet both requirements effectively through centralized policy enforcement.
You have a Microsoft 365 E5 subscription that contains a user named User1 and a web app named App1. App1 must only accept modern authentication requests. You plan to create a Conditional Access policy named CAPolicy1 that will have the following settings: Assignments – Users or workload identities: User1 Cloud apps or actions: App1 – Access controls – Grant: Block access – You need to block only legacy authentication requests to App1. Which condition should you add to CAPolicy1?
Filter for devices
Device platforms
User risk
Sign-in risk
Client apps
The correct answer is E. Client apps because this condition allows you to distinguish between modern authentication (like OAuth 2.0) and legacy authentication (such as basic authentication protocols like POP, IMAP, and older Office clients). In Conditional Access policies, selecting the Client apps condition lets you specifically target legacy authentication clients and apply access controls such as blocking access, without affecting users who authenticate with secure, modern methods. This approach ensures that App1 only accepts modern authentication as required, while blocking legacy sign-in attempts for User1, making it the most precise and effective choice.
You have a Microsoft 365 E5 subscription that contains 100 iOS devices enrolled in Microsoft Intune. You need to deploy a custom line-of-business (LOB) app to the devices by using Intune. Which extension should you select for the app package file?
.intunemac
.ipa
.apk
.appx
Explanation: To deploy a custom Line-of-Business (LOB) app to iOS devices using Microsoft Intune, the app must be in the .ipa (iOS App Store Package) format. What is a .ipa file? .ipa stands for iOS App Store Package. It is the standard packaging format for iOS apps, whether published via the App Store or deployed internally via MDM solutions like Intune. For LOB deployment, the .ipa file must be signed with a valid enterprise distribution certificate (for internal use).
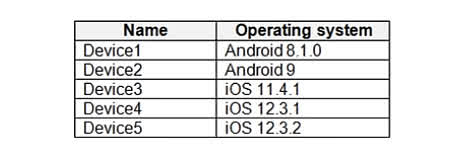
You have a Microsoft Intune subscription. You have devices enrolled in Intune as shown in the following table. An app named App1 is installed on each device. What is the minimum number of app configuration policies required to manage App 1?
1
2
3
4
5
Explanation: App configuration policies in Microsoft Intune are platform-specific, not OS-version specific. In the table: Devices 1 and 2 run Android. Devices 3, 4, and 5 run iOS. Therefore, you only need: 1 policy for Android devices 1 policy for iOS devices
You have a Microsoft 365 E5 subscription that uses Microsoft Intune. You plan to use the Require device to be marked as compliant setting in a Conditional Access policy. You need to ensure that device compliance is evaluated. What should you do first?
Create and assign security baseline profile in Intune.
Enroll devices to Intune.
Join devices to Microsoft Entra ID.
Register devices in Microsoft Entra ID.
Device compliance policies in Intune can only be evaluated for devices that are enrolled in Intune. Enrolling devices is the first step to ensure that compliance policies are applied and that the device’s compliance status can be checked for Conditional Access. Without enrollment, Intune cannot manage or evaluate the device’s compliance.
You have a Microsoft 365 subscription that uses Microsoft Intune Suite. You use Microsoft Intune to manage devices. You plan to deploy two apps named App1 and App2 to all Windows devices. App1 must be installed before App2. From the Intune admin center, you create and deploy two Windows app (Win32) apps. You need to ensure that App1 is installed before App2 on every device. What should you configure?
the App1 deployment configurations
a dynamic device group
a detection rule
the App2 deployment configurations
In Microsoft Intune, when managing Win32 apps, you can define app dependencies. This means you can configure one app (e.g., App2) to depend on another app (e.g., App1) being installed first. ?? You configure app dependencies within the deployment configuration of the dependent app, which in this case is App2. When deploying App2, you specify that App1 is a required dependency. Intune will automatically install App1 first, and only after it is successfully installed, it will proceed to install App2.
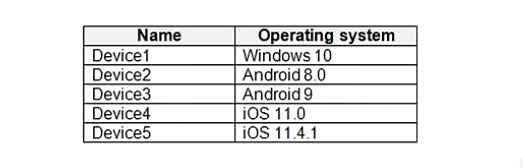
You have an Azure AD tenant named contoso.com that contains the devices shown in the following table. All devices contain an app named App1 and are enrolled in Microsoft Intune. You need to prevent users from copying data from App1 and pasting the data into other apps. Which type of policy and how many policies should you create in Intune? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
To view the answer, Click ” Show Explanation.”
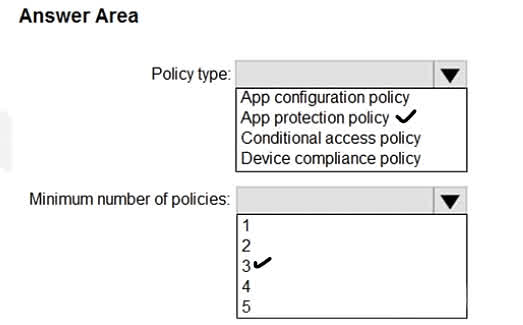
Correct Answer: Policy type: App protection policy Minimum number of policies: 3 Scenario Recap: You have 5 devices with the following OS: Device1: Windows 10 Device2: Android 8.0 Device3: Android 9 Device4: iOS 11.0 Device5: iOS 11.4.1 All devices have App1 installed and are enrolled in Microsoft Intune. You want to prevent users from copying data from App1 to other apps, which is a data protection requirement. Why “App Protection Policy”? App Protection Policies (APP) are specifically designed to: Control data transfer between apps. Enforce copy/paste restrictions, encryption, PIN requirements, etc. These policies apply regardless of whether the device is enrolled or not (as long as it’s managed or has the supported app). This makes it the correct type of policy when you want to restrict data sharing or prevent copy-paste between managed and unmanaged apps. ? Why 3 Policies? App protection policies must be platform-specific, and in this case, you have three OS groups: Windows 10 (Device1) Android (Device2 and Device3) iOS (Device4 and Device5) Each platform requires its own App Protection Policy, so you need: 1 policy for Windows 1 policy for Android 1 policy for iOS Even though some OS versions are different (like Android 8 and 9), one policy can cover all supported versions of that platform. ? Conclusion: Use App Protection Policy to prevent data copying/pasting between apps. Create 3 separate policies, one each for Windows, Android, and iOS.
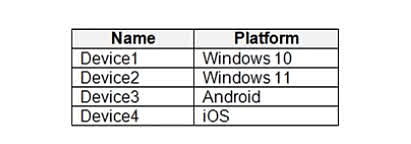
You have devices enrolled in Microsoft Intune as shown in the following table. On which devices can you apply app configuration policies?
Device2 only
Device1 and Device2 only
Device3 and Device4 only
Device2, Device3, and Device4 only
Device1, Device2, Device3 and Device4
App configuration policies in Microsoft Intune are designed to manage settings inside mobile apps (like Outlook, Edge, or Teams) ? and are supported only on mobile platforms: Android (Device3) ? Supported iOS (Device4) ? Supported Windows devices (Device1: Windows 10 and Device2: Windows 11) ? do not support these app configuration policies in the same way. They use different configuration methods like device configuration profiles, not mobile app policies.
Your company has recently implemented Microsoft Intune to manage their fleet of Windows 10 and Windows 11 devices. They want to ensure that all devices use a strong two-factor authentication mechanism to enhance security. You need to configure the devices to replace passwords with a more secure authentication method. How should you configure the devices to implement this secure authentication method?
Configure Windows Hello for Business in the Account protection profile.
Create a VPN profile with two-factor authentication.
Enable Credential Guard in the Endpoint protection profile.
Set up a custom OMA-URI profile for password policies.
Windows Hello for Business provides a strong, passwordless authentication method using biometrics or PIN, combined with device-based two-factor authentication. Configuring it in the Account protection profile through Intune ensures all managed Windows 10 and 11 devices use this secure authentication method, replacing traditional passwords and enhancing security across the organization.
Your company is using Microsoft Intune to manage their devices. They want to create a dynamic group that automatically includes all devices running iOS 11 or older to apply specific security policies. You need to create a dynamic group for these devices. Which membership rule should you use?
device.deviceOSVersion -contains ‘iOS’
device.deviceOSVersion -eq ‘iOS 11’
device.deviceOSVersion -ge ‘11.0’
device.deviceOSVersion -le ‘11.0’
The rule device.deviceOSVersion -le ‘11.0’ will include all devices with an OS version less than or equal to 11.0, which matches the requirement to target devices running iOS 11 or older. This ensures that only the intended devices are included in the dynamic group for applying specific security policies.
Your company is implementing a BYOD policy for employees using Android devices. They need to ensure that work and personal data remain separate on these devices. You need to configure the appropriate enrollment profile for these Android devices. Which enrollment profile should you configure?
Android Enterprise dedicated
Android Enterprise fully managed
Android Enterprise work profile
Device Enrollment Manager (DEM)
The Android Enterprise work profile is specifically designed for BYOD scenarios. It creates a separate, secure container for work data and apps on the user’s personal device, ensuring that work and personal data remain isolated. This allows IT to manage only the work profile, protecting company data while respecting user privacy on their personal device.
