License
Get Microsoft 365 Business Premium License.
Login to Microsoft 365 Admin Center.
Add Custom Domain
Verify your domain by adding a TXT record.
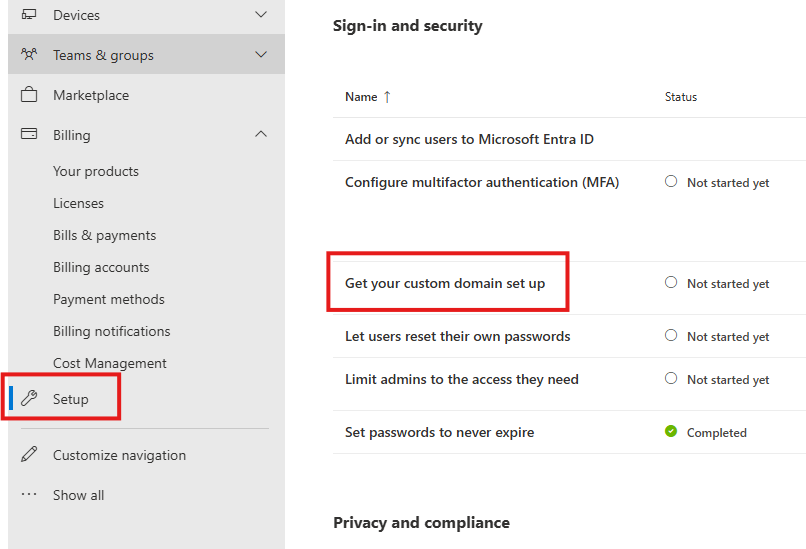
Choose How To Connect Your Domain
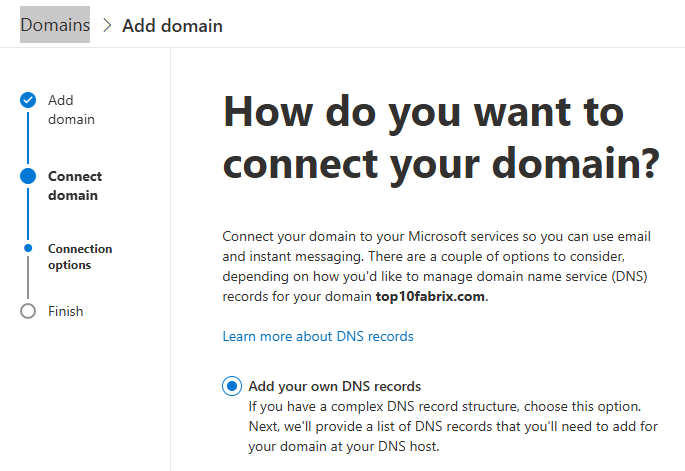
Choose : Add your own DNS record.
Add all DNS record for all the services, like Intune MD, Exchange etc.
Once DNS record are added and verified we will see all our domains :
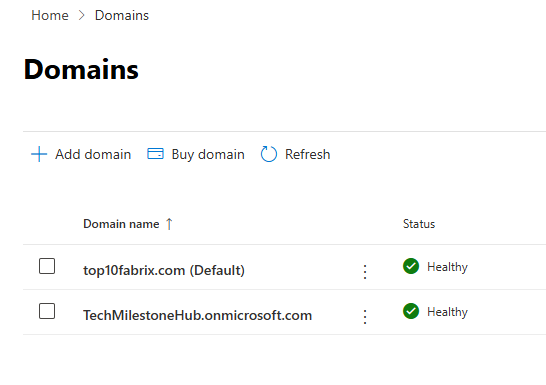
Make the custom domain default, if not already.
Add Users
There will by default 1 user which is privileged user with global administrator role. We have to add more regular users without admin role in our default domain.
Go to User > Active User
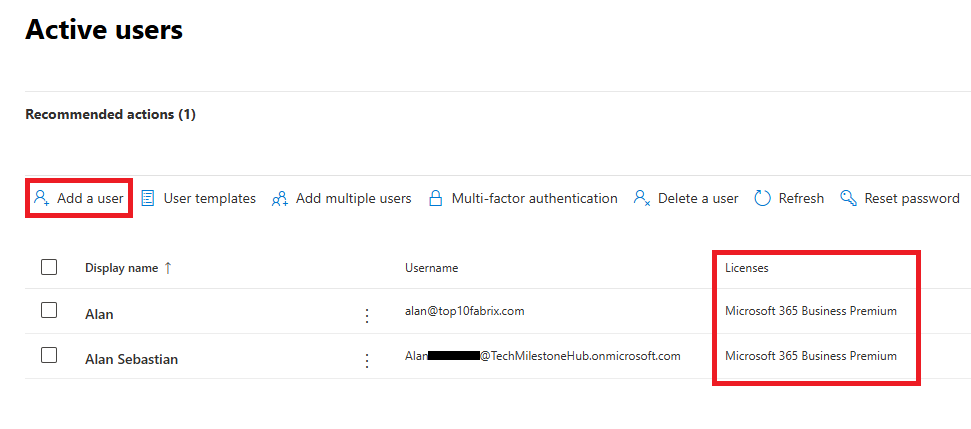
While creating user assign the Microsoft 365 Business Premium license to each user
We should have an additional privileged user with global administrator role, called Emergency access account or break glass account. This account will not have MFA, but use complex password. The user name of this account should also sound discrete, like a usual name.
Automatic Enrollment
Go to : intune.microsoft.com
Devices > Windows Devices > Enrollment > Automatic Enrollment
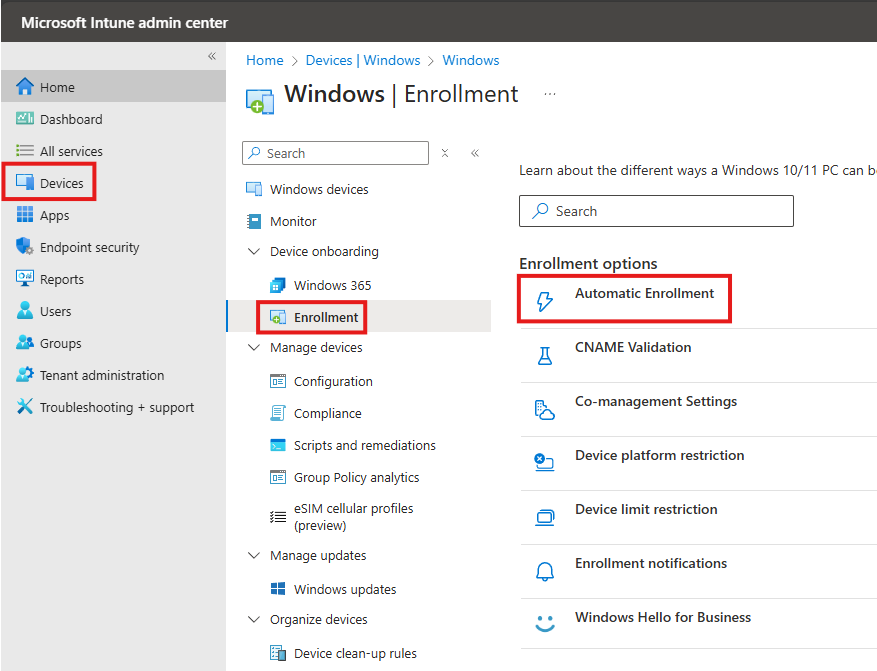
Here we set MDM user scope to all, allowing all users to enroll devices.
Windows Information Protection (WIP) user scope, will be set to none, because it is related to bring your own device.
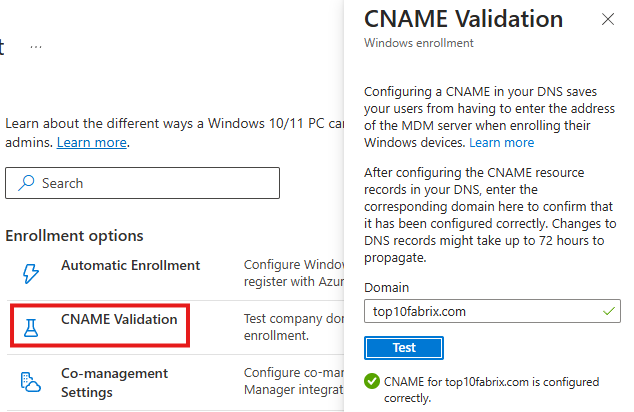
CNAME Validation
This is to check if the custom domain we added is configured correctly.
Device Platform Restriction
Co-Management settings is for SCCM, so that SCCM and Intune can manage device. We will not be doing that.
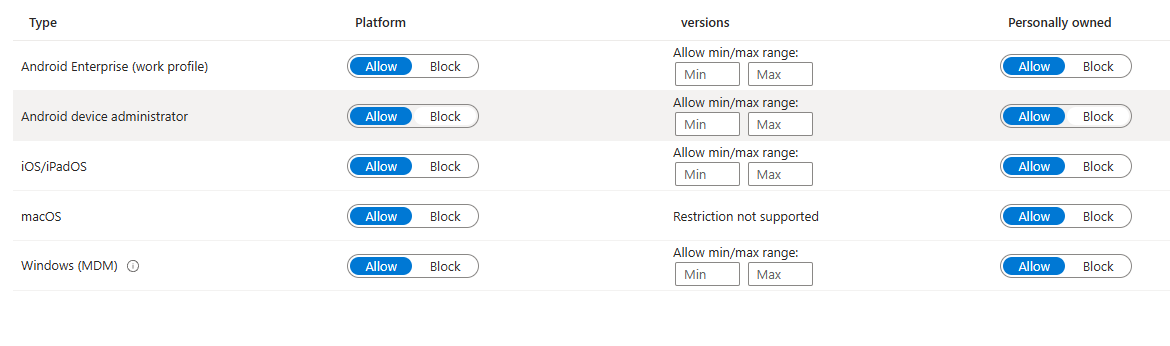
Device Platform Restriction, we can restrict type of devices that we can enroll.
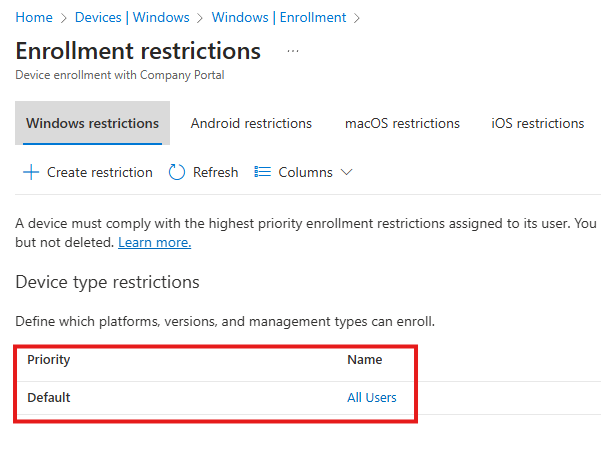
There will be a default policy called : All Users
We can go into properties and edit the policy to block enrollment based on platform and ownership.
Device Limit Restriction
Decides how many devices can be enrolled. This also given as a policy with a name. Click on it : properties > Edit, increase the limit.
Enrollment Notification
To notify user when they enroll device; This is to give them some instructions or for security if anyone else enrolled it.
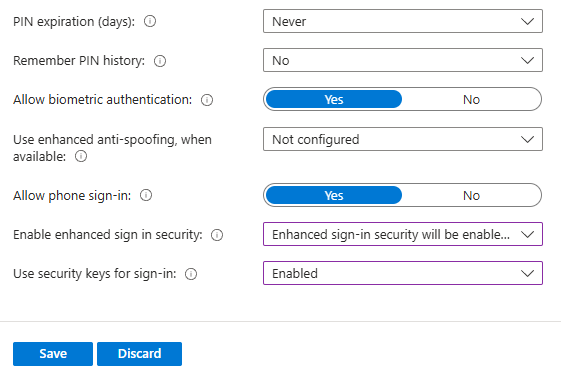
Windows Hello For Business
This is a setting for entire tenant.
Windows Hello for Business settings lets users access their devices using a gesture, such as biometric authentication, or a PIN
Configuration Using Template
Here there will many predefined templates. For example template called endpoint will be about security and firewall, template called kiosk , will be to configure computer as a kiosk, etc.
We will be selecting a template called: Wi-Fi, that will configure a Wi-Fi network.
Select the template and click create.
Name : Office Wi-Fi Configuration
Description: This configuration assigns automatic connection to the office Wi-Fi.
Enable: Connect automatically when in range
Setting Connect to this network, even when it is not broadcasting its SSID, will let us connect even when Wi-Fi is not broadcasting.
We also have to Wi-Fi pre shared key, proxy setting etc.
Assignment Tab
Here we can include or exclude groups for the configuration to apply.
Applicability Rules Tab
Here we can select the conditions for this configuration to apply, like version of windows
Configure Using Setting Catalog
Here, we start from scratch and select settings you want from the library of available settings
We can create a configuration to set desktop background.
Give a meaningful name and description.
Configuration Setting Tab
Here we can Add Settings.
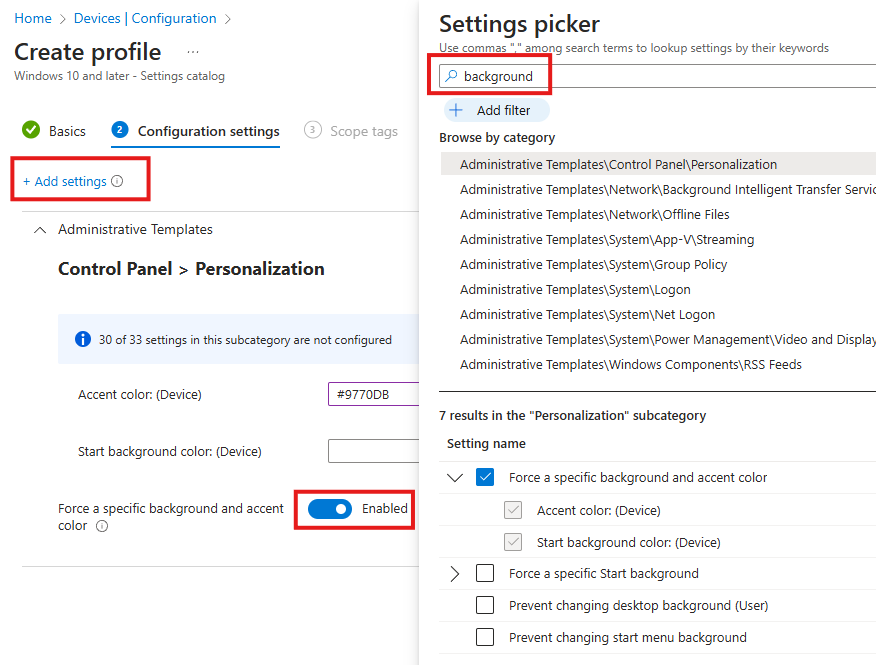
We can search for a setting and choose from category; Whatever we choose will be added to settings catalog on the left side, and view can be collapsed based on category..
Configure Using OMA-URI
If requirement cannot be satisfied by template or settings catalog, we use this.
CSPs (Configuration Service Providers) expose device configuration settings in Windows client.
They use Open Mobile Alliance URIs, which are paths to specific settings in Winidows.
Policy has user scope and a device scope.
Go to : Policy CSP | Microsoft Learn
User scope:
- ./User/Vendor/MSFT/Policy/Config/AreaName/PolicyName to configure the policy.
- ./User/Vendor/MSFT/Policy/Result/AreaName/PolicyName to get the result.
Device scope:
- ./Device/Vendor/MSFT/Policy/Config/AreaName/PolicyName to configure the policy.
- ./Device/Vendor/MSFT/Policy/Result/AreaName/PolicyName to get the result.
Set Lock Screen Image
Search in MS page and find the path
We will be configuring: EnforceLockScreenAndLogonImage
./Device/Vendor/MSFT/Policy/Config/DeviceLock/EnforceLockScreenAndLogonImage
Go to Device > Configuration > Create New Policy > Select template : Custom
In the Configuration settings tab click : Add Row:
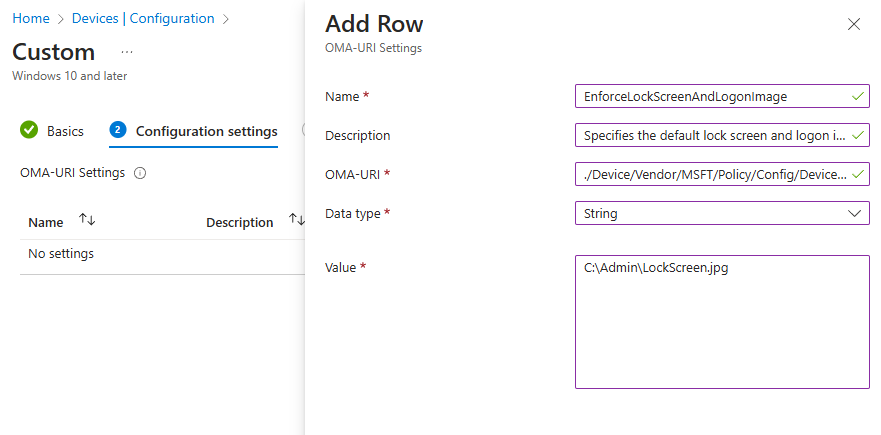
Put the OMA-URI we found on the Microsoft page, with the required value, which is in our case path to the image file or we can also use image CDN.
Configure Endpoint Security
Create a template configuration and select : Endpoint protection
In the configuration settings tab, we can see many setting that is available for configuration for endpoint security.
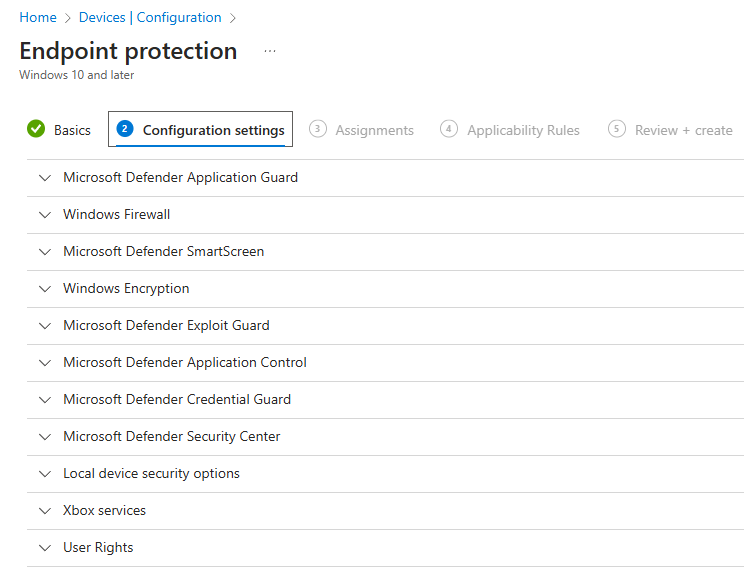
Here best practice is to configure only 1 settings in each policy and give a meaningful name.
Endpoint Security
Better than creating a configuration for End Point Security, in Intune there is a section called Endpoint Security.
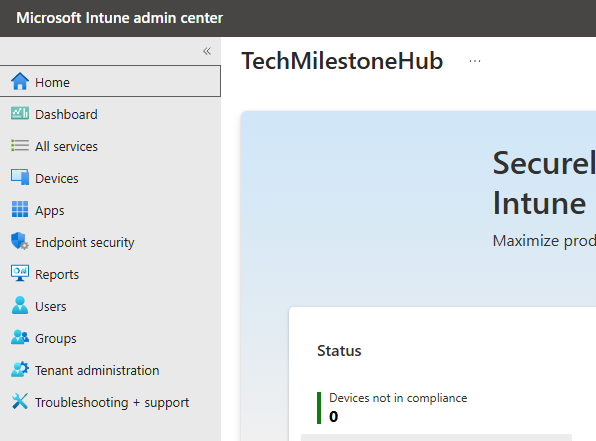
Here there are specific endpoint security areas we can configure an monitor. It will show the health of devices that has received this policy.
Antivirus
In Endpoint Security, we can create anti-virus policy.
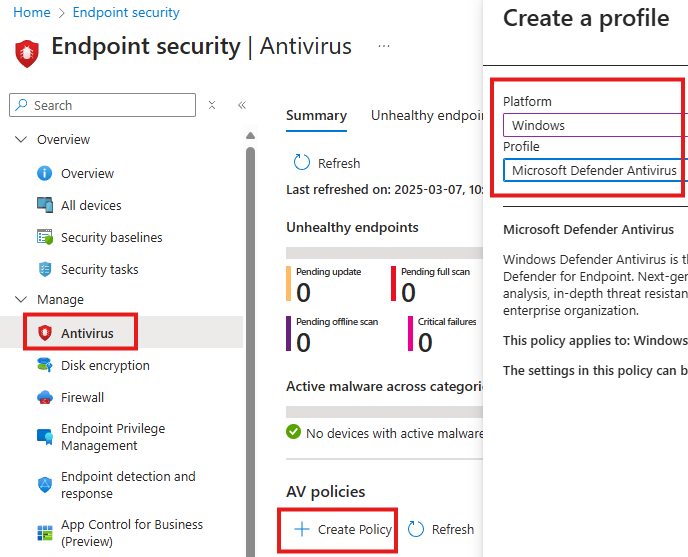
In the configuration settings tab of the policy we will get all available settings we can configure.
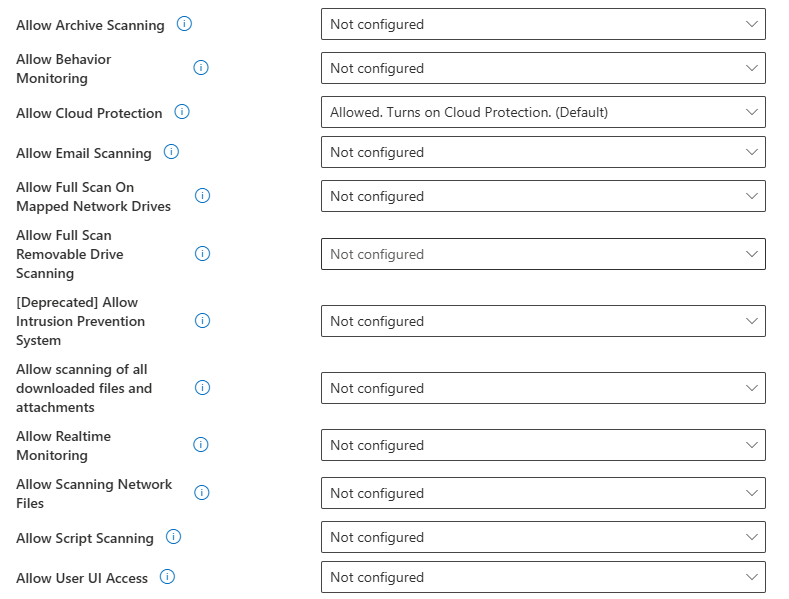
Even If we create the policy here, it will be also reflected in : Windows Device configurations as a policy.
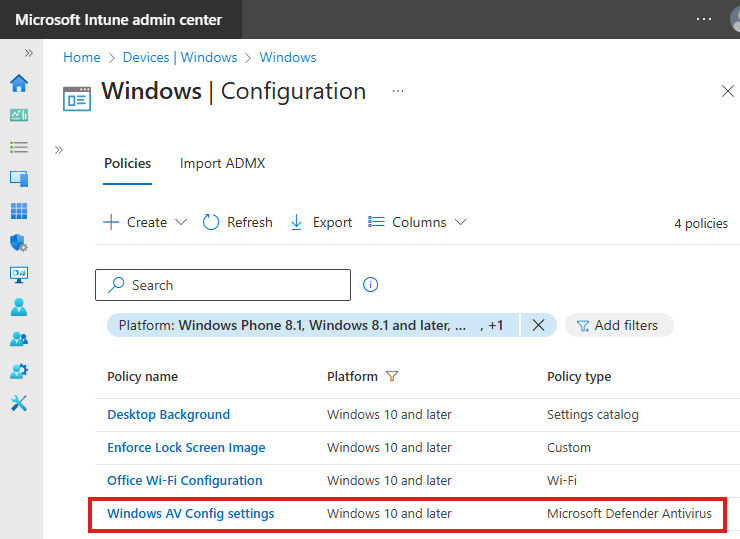
Check that: Go to Devices > Windows > Configurations
Bit-Locker
Go to : Endpoint Security > Disk Encryption > Create Policy : Select Windows, Bitlocker.
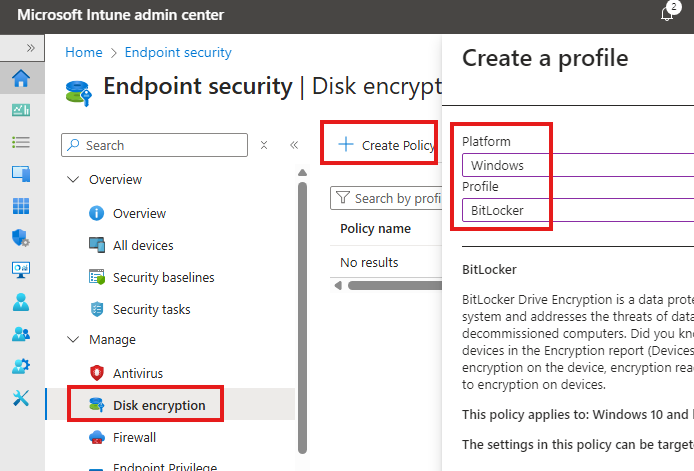
Click Create
In the configuration tab of the policy, we can see various settings we can configure.
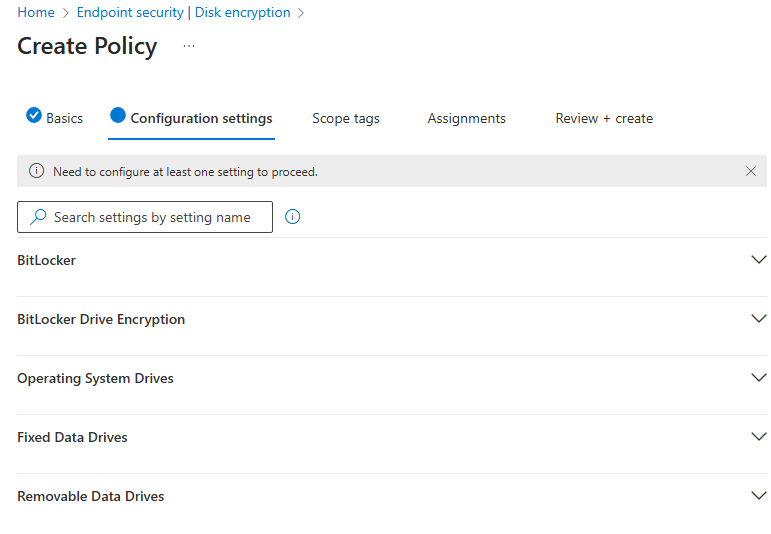
Bit-locker user TMP module in the machine hardware. We can also configure to use bit locker without TPM module here.
Firewall
Go to : Endpoint Security > Firewall > Create Policy
Some settings available for configuration are:
Configure App Control for Business
Go to : Endpoint Security > App Control for Business > Create Policy
This to allow/block certain applications in the device.
Here we can set configuration as XML file of use built-in controls(can cause re-boot). With XML we can block the reboot.
We can make device trust apps from managed installers.
To make Intune as managed installer we need to add.
Configure Device Compliance
Policy that checks if device in an organization meets certain requirements.
Device > Windows > Compliance
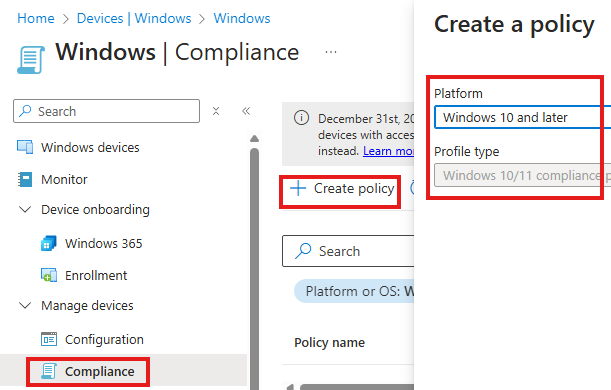
Various available categories for checking compliance can be see in Compliance settings tab.
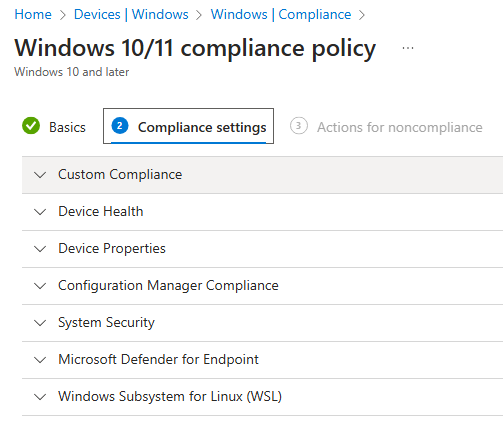
We can also set actions on non compliance like, what to do if device is not compliant
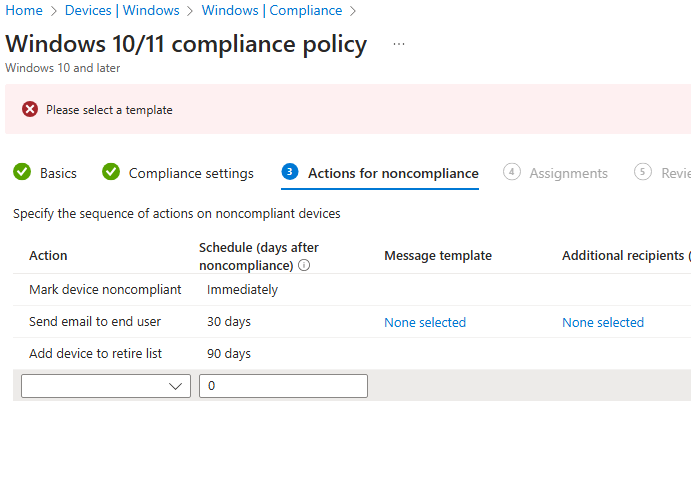
We can sent email to user to let them know that device is non-compliant, so best practice is to have only 1 setting in 1 policy, so that in the message we can say what settings need to be addressed.
Here we are installing application from Winget repository, where Microsoft store app (new) apps binaries are located
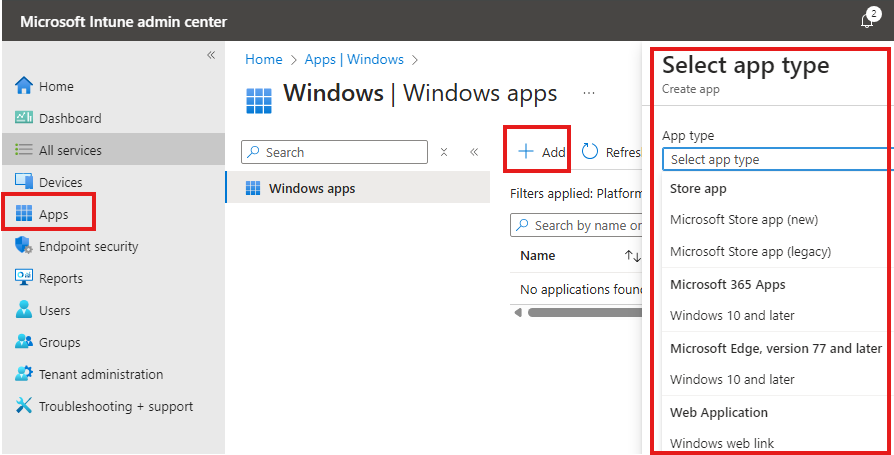
Here we are selecting the app type. If we choose Microsoft store app (new)
Once we select the app type we can search for the app.
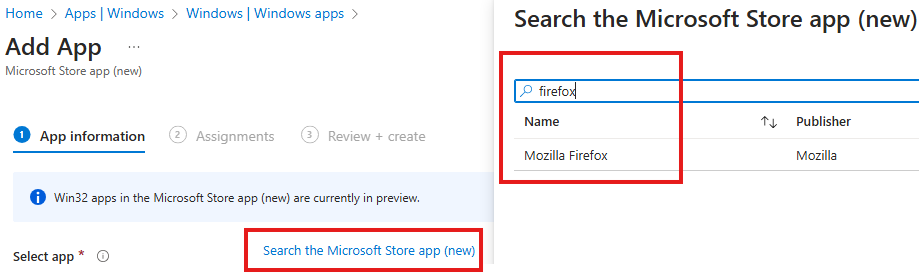
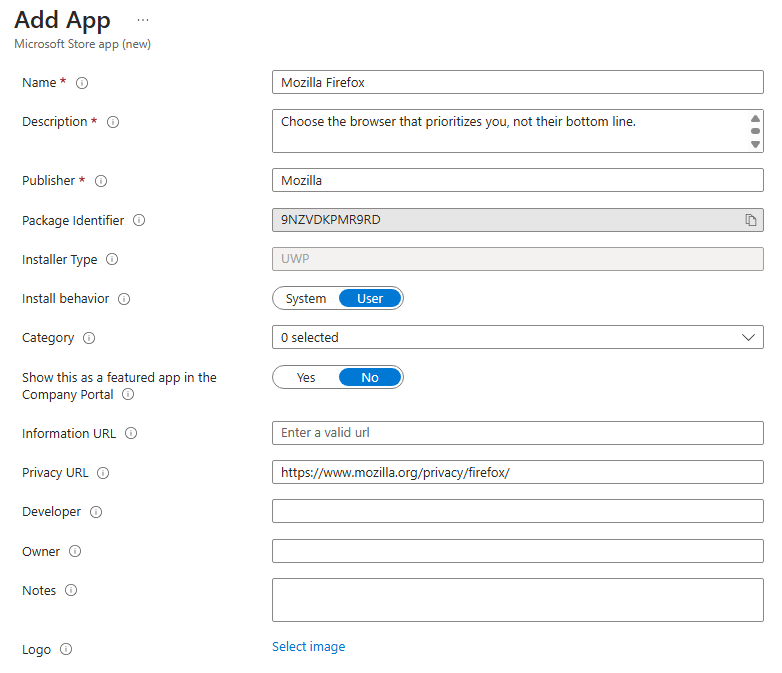
Then we can set the app meta information
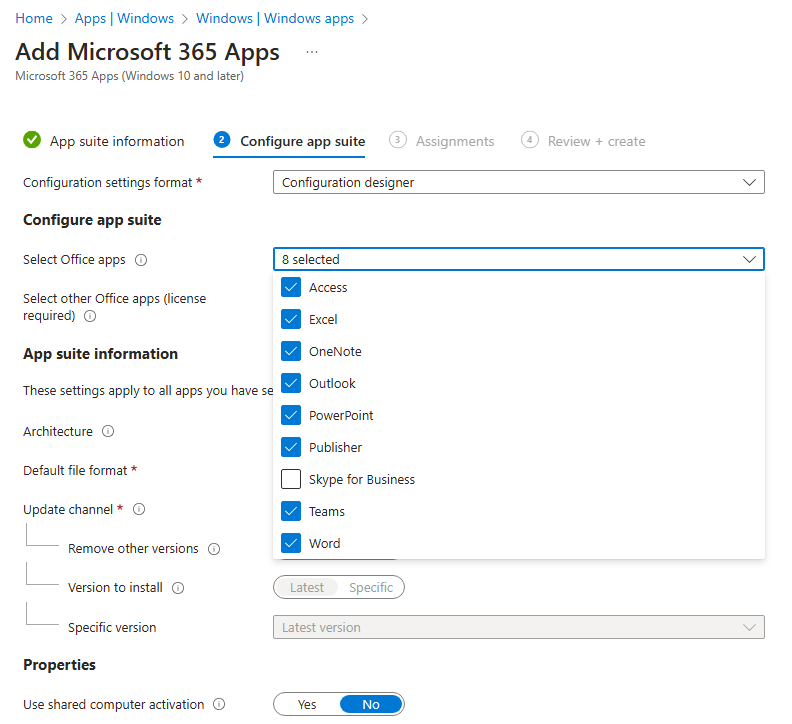
Deploy Microsoft 365 Apps For Enterprise
Select Microsoft 365 app
Here in the configuration tab, we can select the Microsoft 365 Apps we need.
Web Application Shortcuts on Start Menu
Same way we deployed other app we can selected app type of Web application shortcut.
Deploy Line Of Business Application
LOB Apps are apps built by the organization.
We have to select the installer that we packaged.
Deploy Win32 Application
These are binaries of app with extension “.intinewin”.
We need to converted our “.exe” binaries to “.intinewin”, for that we need a utility that can be downloaded from Microsoft website, called IntuneWinApp.exe
While creating the application we can select the commands for installation and uninstallation. Also select some status codes for installation.
Detection Rules
Detection rules can be set while deploying Win32 Apps. It means a condition that will satisfy that will indicate that the app is installed;
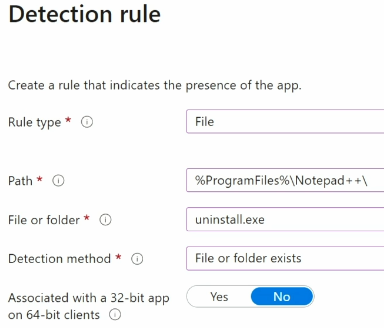
For example presence of uninstall.exe in the installation location, will indicate that app is installed in the system.
Another detection method is a registry value that will be added when app is installed.
Dependency
Here we can select the Win 32 apps that will dependent on this application.
Supersede
Here we specify the apps that will be replaced by this application. For example, lower versions will be replaced with a higher version.
Deploy App Using 3-party Robo pack
Robo pack can connect directly to Intune tenant. It will create Detection Rules.
Robopatch flow
Other than regular deploying, we can also setup Robopatch flow. It will look for updated version of the application and will deploy it automatically.
We can deploy in waves, we can select different groups in each wave.
Deploy Custom Apps With Robo pack
We can upload and convert package.
