You have a Microsoft 365 tenant and an Azure Active Directory (Azure AD) tenant named contoso.com. You plan to grant three users named User1, User2, and User3 access to a temporary Microsoft SharePoint document library named Library1. You need to create groups for the users. The solution must ensure that the groups are deleted automatically after 180 days. Which two groups should you create? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
a Microsoft 365 group that uses the Assigned membership type
a Security group that uses the Assigned membership type
a Microsoft 365 group that uses the Dynamic User membership type
a Security group that uses the Dynamic User membership type
a Security group that uses the Dynamic Device membership type
To meet the requirement of automatically deleting groups after 180 days, we must use Microsoft 365 groups because they support expiration policies in Azure Active Directory (Azure AD). Security groups do not support expiration policies. Why is (a) Correct? ? Microsoft 365 Group (Assigned Membership) Supports expiration policies, so it can be automatically deleted after 180 days. Assigned membership allows an admin to manually add User1, User2, and User3 to the group. Best when users need to be manually managed. Why is (c) Correct? ? Microsoft 365 Group (Dynamic User Membership) Supports expiration policies, ensuring automatic deletion after 180 days. Dynamic User membership automatically adds/removes users based on Azure AD rules (e.g., if their department is “Finance” or job title is “Analyst”). Best when access needs to be automated based on attributes. Why Are the Other Options Incorrect? ? (b) A Security group that uses the Assigned membership type Security groups do NOT support expiration policies, meaning they won’t be deleted automatically after 180 days. ? (d) A Security group that uses the Dynamic User membership type Security groups do NOT support expiration policies, even if they use dynamic user membership. ? (e) A Security group that uses the Dynamic Device membership type Device-based membership is irrelevant since we are managing users, not devices. Security groups do NOT support expiration policies.
You have an Azure subscription. Users access the resources in the subscription from either home or from customer sites. From home, users must establish a point-to-site VPN to access the Azure resources. The users on the customer sites access the Azure resources by using site-to-site VPNs. You have a line-of-business app named App1 that runs on several Azure virtual machines. The virtual machines run Windows Server 2016. You need to ensure that the connections to App1 are spread across all the virtual machines. What are two possible Azure services that you can use? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
an internal load balancer
a public load balancer
an Azure Content Delivery Network (CDN)
Traffic Manager
an Azure Application Gateway
Your goal is to distribute incoming traffic for App1, which is running on multiple Azure virtual machines (VMs). Since users connect via VPN (Point-to-Site and Site-to-Site), the traffic remains within the Azure private network, meaning public-facing solutions (like a public load balancer or CDN) are not needed. The two best options for load balancing private network traffic are: 1?? Internal Load Balancer (ILB) Why? An Internal Load Balancer (ILB) is designed for private network traffic within Azure. It distributes traffic only inside a Virtual Network (VNet) without exposing resources to the internet. Since users connect over a VPN (which extends their network to Azure), ILB ensures that their requests are properly balanced across all VMs running App1. 2?? Azure Application Gateway Why? Application Gateway is a layer 7 (HTTP/HTTPS) load balancer that distributes web traffic across VMs. It provides features like SSL termination, cookie-based session affinity, and Web Application Firewall (WAF). If App1 is a web application, this is a great choice as it optimizes and secures HTTP/S traffic. Why Not the Other Options? ? (b) A Public Load Balancer A public load balancer distributes traffic from the internet to Azure resources. Since users connect via VPN, the traffic is private, so a public load balancer is not needed. ? (c) Azure Content Delivery Network (CDN) CDN is used for caching static content (e.g., images, videos, scripts) and delivering it to users with lower latency. It does not distribute requests to VMs running App1. ? (d) Traffic Manager Traffic Manager is a DNS-based global traffic routing service. It is used to route traffic across multiple Azure regions but does not distribute traffic among VMs within a VNet.
You have a Microsoft 365 tenant and an Azure Active Directory (Azure AD) tenant named contoso.com. You plan to grant three users named User1, User2, and User3 access to a temporary Microsoft SharePoint document library named Library1. You need to create groups for the users. The solution must ensure that the groups are deleted automatically after 180 days. Which two groups should you create? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
an Office 365 group that uses the Assigned membership type
a Security group that uses the Assigned membership type
an Office 365 group that uses the Dynamic User membership type
Security group that uses the Dynamic User membership type
a Security group that uses the Dynamic Device membership type
To grant temporary access to a Microsoft SharePoint document library (Library1) while ensuring that the groups are automatically deleted after 180 days, you need to use Microsoft 365 Groups (formerly Office 365 Groups) with an expiration policy. Microsoft 365 (Office 365) Groups support expiration policies, which allow groups to be automatically deleted after a set period (e.g., 180 days) unless renewed. Security groups do not support this feature. Why These Two Options? 1?? “An Office 365 group that uses the Assigned membership type” This allows manual assignment of specific users (User1, User2, and User3) to the group. The group can be configured with an expiration policy (e.g., 180 days). Since it’s a Microsoft 365 Group, it is fully integrated with SharePoint, making it the best option for granting access to a SharePoint document library. 2?? “An Office 365 group that uses the Dynamic User membership type” This allows users to be automatically added or removed from the group based on attributes (e.g., department, job title). The group will also expire after 180 days if an expiration policy is applied. This is useful if users should be added to the group dynamically without manual intervention. Why Not the Other Options? “A Security group that uses the Assigned membership type” Security groups do not support expiration policies in Azure AD. Even though security groups can be used for SharePoint permissions, they won’t be automatically deleted after 180 days. “A Security group that uses the Dynamic User membership type” Security groups cannot be assigned an expiration policy. Dynamic user membership only helps with automatic user management, but it does not meet the requirement for automatic deletion. “A Security group that uses the Dynamic Device membership type” This is for managing devices (not users). Device-based security groups have no relevance to SharePoint permissions.
Your company has an Azure subscription that includes a Recovery Services vault. You want to use Azure Backup to schedule a backup of your company’s virtual machines (VMs) to the Recovery Services vault. Which of the following VMs can you back up? (Choose all that apply)
VMs that run Windows 10
VMs that run Windows Server 2012 or higher
VMs that have NOT been shut down
VMs that run Debian 8.2+
VMs that have been shut down
Azure Backup, through the Recovery Services vault, allows backing up virtual machines regardless of their OS version, power state, or type (Windows or Linux). Let’s analyze each option: ? (a) VMs that run Windows 10 Supported: Yes, Azure Backup supports Windows 10 (Enterprise, Pro, and Education editions). Limitation: Windows 10 Home edition is not supported in Azure VM scenarios. ? (b) VMs that run Windows Server 2012 or higher Supported: Yes, Windows Server 2012, 2016, 2019, and 2022 are all supported for Azure Backup. Why? Azure Backup fully integrates with Windows Server operating systems for backups at the VM level and file/folder level. ? (c) VMs that have NOT been shut down Supported: Yes, running VMs can be backed up without downtime. How? Azure Backup takes snapshots while the VM is running, ensuring minimal disruption. ? (d) VMs that run Debian 8.2+ Supported: Yes, Azure Backup supports many Linux distributions, including: Debian 8.2 and higher Ubuntu CentOS Red Hat Enterprise Linux (RHEL) SUSE Linux Enterprise Server (SLES) Oracle Linux Why? Azure Backup uses the Linux VM agent to take snapshots and perform backups. ? (e) VMs that have been shut down Supported: Yes, even stopped (deallocated) VMs can be backed up. How? Azure Backup captures snapshots of the disks, meaning the VM does not have to be running. Benefit? This helps save costs, as deallocated VMs do not incur compute charges but can still be backed up.
You have an Azure subscription that contains the following virtual networks: + VNet1 has an IP address range of 196.162.0.0/24. + VNet2 has an IP address range of 10.10.0.0/24. + VNet3 has an IP address range of 196.162.0.0/16. You need to configure virtual network peering. Which two peering can you create? Each correct answer presents a complete solution
VNET1 can be peered with VNET2
VNET1 can be peered with VNET3
VNET2 can be peered with VNET3
VNET3 can be peered with VNET1
Azure Virtual Network Peering allows virtual networks (VNets) to connect and communicate as if they were a single network. However, there is a key requirement: VNets cannot be peered if they have overlapping IP address ranges. Step-by-Step Peering Analysis: VNet1 (196.162.0.0/24) and VNet2 (10.10.0.0/24) ? ? Peering Allowed These two VNets have different, non-overlapping IP address ranges, so they can be peered. VNet1 (196.162.0.0/24) and VNet3 (196.162.0.0/16) ? ? Peering NOT Allowed VNet3’s IP range (196.162.0.0/16) overlaps with VNet1’s IP range (196.162.0.0/24). Because of this overlap, Azure does not allow peering between these two VNets. VNet2 (10.10.0.0/24) and VNet3 (196.162.0.0/16) ? ? Peering Allowed These two VNets have different, non-overlapping IP address ranges, so they can be peered. VNet3 (196.162.0.0/16) and VNet1 (196.162.0.0/24) ? ? Peering NOT Allowed This is the same as scenario #2. IP range overlap prevents peering.
You are evaluating the connectivity between the virtual machines after the planned implementation of the Azure networking infrastructure. For each of the following statements, select the correct.
The virtual machines on Subnet1 will be able to connect to the virtual machines on Subnet3
The virtual machines on ClientSubnet will be able to connect to the internet.
The virtual machines on Subnet3 and Subnet4 will be able to connect to the internet
In an Azure networking infrastructure, connectivity between virtual machines (VMs) depends on various factors such as Virtual Network (VNet) configurations, Network Security Groups (NSGs), Route Tables, and whether a NAT Gateway or Public IP is assigned. Here’s why all the given statements are correct: The virtual machines on Subnet1 will be able to connect to the virtual machines on Subnet3 – YES By default, all subnets within the same Virtual Network (VNet) in Azure can communicate with each other unless explicitly restricted by NSGs or custom route tables. If Subnet1 and Subnet3 are part of the same VNet and there are no NSG rules blocking traffic, the VMs will be able to communicate. The virtual machines on ClientSubnet will be able to connect to the internet – YES Azure provides internet access by default to all VMs that have a valid outbound internet connection via a default route (0.0.0.0/0) and no blocking NSG rules. If ClientSubnet has no NSG rules denying outbound traffic and no custom route table redirecting internet-bound traffic elsewhere, then the VMs can connect to the internet. The virtual machines on Subnet3 and Subnet4 will be able to connect to the internet – YES Similar to ClientSubnet, if Subnet3 and Subnet4 do not have NSG rules blocking outbound traffic and they follow the default Azure internet connectivity setup, they will have internet access. Azure’s default route (0.0.0.0/0) allows outbound internet traffic unless modified by a custom route table or NSG.
You host a service with two Azure virtual machines. You discover that occasional outages cause your service to fail. What two actions can you do to minimize the impact of the outages? Select two options
Add a load balancer
Put the virtual machines in a scale set
Put the virtual machines in an availability set
Add a network gate
Add a third instance of the virtual machine
Since your service is experiencing occasional outages, the goal is to improve availability and fault tolerance. The best way to achieve this is by ensuring redundancy and load distribution across multiple VMs. 1. Add a Load Balancer An Azure Load Balancer helps by distributing traffic between VMs. If one VM goes down due to an outage, the load balancer will redirect traffic to the other available VM. This ensures that the service remains accessible even if a single VM fails. 2. Put the Virtual Machines in an Availability Set An Availability Set protects against hardware failures within a single datacenter by distributing VMs across multiple Fault Domains (FDs) and Update Domains (UDs). Fault Domains ensure that VMs are placed in different physical racks to prevent failure from a single hardware issue. Update Domains ensure that VMs are updated one at a time to prevent downtime during maintenance. If one physical server fails, the other VM in the availability set remains operational, reducing the impact of outages. Why Other Options Are Incorrect? (b) Put the virtual machines in a scale set A scale set is mainly for handling traffic spikes by automatically adding/removing VMs. It does not directly protect against outages due to hardware failures, making an availability set a better choice for high availability. (d) Add a network gateway A network gateway is used for VPN connections and hybrid cloud setups. It does not help with improving availability or preventing service failure. (e) Add a third instance of the virtual machine While adding another VM increases redundancy, it does not prevent outages unless they are placed in an Availability Set. Without a load balancer, traffic cannot be efficiently distributed between the instances.
Your company has a Microsoft 365 tenant and an Azure Active Directory (Azure AD) tenant named contoso.com. The company uses several Azure Files shares. Each share is assigned to a different department at the company. The department attribute in Azure AD is populated for all users. You need to ensure that the users can access the departmental file shares: Which two types of groups should you use?
a security group that uses the dynamic membership type
a Microsoft 365 group that uses the dynamic membership type
a distribution group that uses the dynamic membership type
a security group that uses the assigned membership type
a Microsoft 365 group that uses the assigned membership type
Your goal is to ensure that users can access departmental Azure Files shares based on their department attribute in Azure AD. To achieve this, you need groups that support access control via Azure Role-Based Access Control (RBAC) and Azure AD authentication. Why These Two Options Are Correct? 1. Microsoft 365 Group (Assigned Membership Type) (Option E) Microsoft 365 groups allow manual assignment of users. Admins can manually assign members to their respective departmental file shares. This is useful when users need specific access that doesn’t change dynamically. Microsoft 365 groups also integrate well with OneDrive, SharePoint, and Teams, providing easy access to departmental file shares. 2. Security Group (Dynamic Membership Type) (Option A) A security group with dynamic membership automatically assigns users based on their Azure AD attributes (like “department”). Since all users have the department attribute populated, this ensures that users automatically get assigned to their respective departmental file shares. Dynamic security groups help reduce manual effort and ensure real-time access control as users change departments.
You have a Microsoft 365 tenant and an Azure Active Directory (Azure AD) tenant named contoso.com. You plan to grant three users named User1, User2, and User3 access to a temporary Microsoft SharePoint document library named Library. You need to create groups for the users. The solution must ensure that the groups are deleted automatically after 180 days. Which two groups should you create? Each correct answer presents a complete solution
a Microsoft 365 group that uses the Assigned membership type
A security group that uses the Assigned membership type
a Microsoft 365 group that uses the Dynamic User membership type
A security group that uses the Dynamic User membership type
A security group that uses the Dynamic Device membership type
You need to grant temporary access to a SharePoint document library and ensure that the groups automatically delete after 180 days. The best way to do this is by using groups with dynamic membership and Azure AD access reviews & expiration policies. Why these groups? Microsoft 365 group (Dynamic User membership) Microsoft 365 groups support SharePoint access natively, making them a great choice for managing access to document libraries. Dynamic membership ensures that users are automatically added or removed based on defined rules. Microsoft 365 groups support expiration policies, meaning they can be automatically deleted after 180 days if configured in Azure AD. Security group (Dynamic User membership) Security groups are also a good option for managing access and permissions at a granular level. Dynamic membership ensures only the correct users are part of the group. Security groups can also be set up with expiration policies in Azure AD. Why not the other options? ? (A) Microsoft 365 group with Assigned membership – Requires manual user management and does not automatically remove users. ? (E) Security group with Dynamic Device membership – Manages devices, not users, so it’s irrelevant for SharePoint access.
Your company has a Microsoft 365 tenant and a Microsoft Entra ID tenant named contoso.com. The company uses several Azure Files shares. Each share is assigned to a different department at the company. The department attribute in Microsoft Entra ID is populated for all users. You need to ensure that the users can access the departmental file shares. Which two types of groups should you use? Each correct presentation presents a complete solution.
a security group that uses the dynamic membership ty
a distribution group that uses the dynamic membership type
a Microsoft 365 group that uses the dynamic membership type
a security group that uses the assigned membership type
a Microsoft 365 group that uses the assigned membership type
You need to ensure that users can access Azure File Shares based on their department. The best way to manage this is by using groups with dynamic membership in Microsoft Entra ID (formerly Azure AD). Dynamic groups automatically update their membership based on user attributes (e.g., department), making them ideal for this scenario. Why these two options? ? (a) A security group that uses the dynamic membership type Security groups are used to manage access to Azure resources, including Azure File Shares. A dynamic security group can automatically include users based on the department attribute in Microsoft Entra ID. This ensures users are automatically granted access to the correct file share without manual intervention. ? (c) A Microsoft 365 group that uses the dynamic membership type Microsoft 365 groups provide collaboration features such as Teams, SharePoint, and email, but they can also be used for access management. A dynamic Microsoft 365 group automatically includes users based on the department attribute, ensuring they are assigned to the correct departmental file shares. Why not the other options? ? (b) A distribution group that uses the dynamic membership type Distribution groups are only used for email distribution lists. They cannot be used for granting access to Azure File Shares. ? (d) A security group that uses the assigned membership type Assigned security groups require manual management of group members. Since you need to automatically assign users based on the department attribute, dynamic membership is required. ? (e) A Microsoft 365 group that uses the assigned membership type Just like option (d), assigned groups require manual management instead of dynamic updates based on attributes.
Your company has 10 different departments. You have an Azure subscription that contains several hundred virtual machines. The users of each department use only their department’s virtual machines. You plan to apply resource tags for each department to the virtual machines. Which two solutions should you use? Each correct presentation presents a complete solution.
PowerShell
Azure Resource Manager (ARM) templates
App registrations
Azure Advisor
Applying resource tags to virtual machines (VMs) in Azure helps in organizing, managing, and controlling cost allocation for different departments. Since there are several hundred VMs, an automated approach is required. The two best solutions for applying tags efficiently are: 1?? PowerShell PowerShell can be used to automate the tagging process for multiple VMs at scale. It allows: ? Bulk updates – Apply tags to multiple VMs at once. ? Script execution – You can write a script to assign department-specific tags dynamically. ? Automation – Can be integrated into CI/CD pipelines for automatic tagging. ? Example PowerShell command to add a tag to a VM: $vm = Get-AzVM -ResourceGroupName “RG-Sales” -Name “VM-Sales-01” $vm.Tags.Add(“Department”, “Sales”) Set-AzResource -ResourceId $vm.Id -Tag $vm.Tags -Force 2?? Azure Resource Manager (ARM) Templates ARM templates define resources in JSON format and support tagging resources during deployment. This ensures that tags are applied consistently to new virtual machines. ? Declarative Approach – Tags are assigned at deployment time. ? Consistency – Every VM deployed using this template will have the correct department tag. ? Automation – Can be used in CI/CD pipelines. ? Example ARM template snippet for tagging a VM: { “type”: “Microsoft.Compute/virtualMachines”, “name”: “[parameters(‘vmName’)]”, “apiVersion”: “2021-03-01”, “location”: “[parameters(‘location’)]”, “tags”: { “Department”: “[parameters(‘departmentName’)]” } } Why Not the Other Options? ? App Registrations (Option C) App registrations in Microsoft Entra ID (formerly Azure AD) are used for app authentication and API access, not for tagging resources. ? Azure Advisor (Option D) Azure Advisor provides recommendations on best practices for cost, security, performance, and reliability. It does not apply tags to resources.
You have a Microsoft Entra tenant. You plan to perform a bulk import of users. You need to ensure that imported user objects are added automatically as the members of a specific group based on each user’s department. The solution must minimize administrative effort. Which two actions should you perform? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
Create groups that use the Assigned membership type.
Create an Azure Resource Manager (ARM) template.
Create groups that use the Dynamic User membership type.
Write a PowerShell script that parses an import file.
Create an XML file that contains user information and the appropriate attributes.
Create a CSV file that contains user information and the appropriate attributes.
When performing a bulk import of users into Microsoft Entra ID, you want to automatically assign them to specific groups based on their department attribute. The best way to achieve this with minimal administrative effort is by using: 1?? Dynamic User Membership Type for Groups Microsoft Entra dynamic groups allow automatic membership based on user attributes (e.g., department, job title, location). When a user is created with a specific department in their profile, they will be automatically added to the correct group. This eliminates the need for manual group assignments. Example Dynamic Membership Rule for a group: plaintext Copy Edit (user.department -eq “Sales”) This rule ensures that any user whose department is “Sales” will be automatically assigned to the group. 2?? CSV File for Bulk Import Microsoft Entra ID supports bulk user import using a CSV file. The CSV file contains user details, including attributes like department, which is used for dynamic group membership assignment. Example CSV Format: UserPrincipalName, DisplayName, GivenName, Surname, Mail, Department user1@contoso.com, User One, User, One, user1@contoso.com, Sales user2@contoso.com, User Two, User, Two, user2@contoso.com, HR Once users are imported, they will automatically join the correct dynamic groups based on the department field. Why Not the Other Options? ? (A) Create groups that use the Assigned membership type. Incorrect because assigned groups require manual user assignment and do not dynamically update based on attributes. ? (B) Create an Azure Resource Manager (ARM) template. Incorrect because ARM templates are used for deploying Azure resources (e.g., VMs, storage) but not for bulk user imports. ? (D) Write a PowerShell script that parses an import file. Incorrect because PowerShell scripts would require manual execution each time users are imported, which increases administrative effort. Dynamic user groups automate this process, making PowerShell unnecessary for this scenario. ? (E) Create an XML file that contains user information and the appropriate attributes. Incorrect because Microsoft Entra ID does not support XML for bulk user import. CSV files are the required format.
You have an Azure subscription that contains a storage account named account1. You plan to upload the disk files of a virtual machine to account1 from your on-premises network. The on-premises network uses a public IP address space of 131.107.1.0/24. You plan to use the disk files to provision an Azure virtual machine named VMI. VM1 will be attached to a virtual network named VNet1. VNet1 uses an IP address space of 192.168.0.0/24. You need to configure account1 to meet the following requirements: Ensure that you can upload the disk files to account1 Ensure that you can attach the disks to VM1 Prevent all other access to account1 Which two actions should you perform?
From the firewalls and virtual networks blade of account 1, select Selected networks.
From the Firewalls and virtual networks blade of account1, select Allow trusted Microsoft services to access this storage account.
From the firewalls and virtual networks blade of the account1, add the 131.107.1.0/24 IP address range.
From the Firewalls and virtual networks blade of the account1, add VNet1
From the Service endpoints blade of VNet1, add a service endpoint
You need to configure account1 (an Azure Storage account) to meet the following requirements: Allow uploading of VM disk files from your on-premises network (131.107.1.0/24). Ensure VM1 can access the disks stored in account1. Block all other unauthorized access. Step 1: Restrict Access to Specific Networks By default, storage accounts allow access from all networks. To restrict access: (a) Select “Selected networks” under the “Firewalls and virtual networks” blade of account1. This ensures that only explicitly defined networks can access the storage account. Step 2: Allow Access from On-Premises (Upload Disk Files) Since your on-premises network has the public IP range 131.107.1.0/24, you must: (c) Add the IP range 131.107.1.0/24 under the “Firewalls and virtual networks” settings of account1. This allows your on-premises network to upload disk files while blocking all other public traffic. Why Not the Other Options? (b) Allow trusted Microsoft services to access this storage account ? This option is used for services like Azure Backup, Azure Site Recovery, and Azure SQL. It does not control general network access or allow your on-premises network to upload disk files. (d) Add VNet1 to the firewall settings ? Adding VNet1 would allow Azure Virtual Machines inside that VNet to access account1 directly. However, this is not required for VM1 to attach the disk, because attaching a managed disk does not require direct storage access. (e) Add a service endpoint in VNet1 ? Service endpoints allow private access to the storage account from within Azure VNets. However, your requirement is to upload disk files from an on-premises network, not from an Azure VNet.
You have an Azure subscription that contains the resources in the following table. Store1 contains a file share named data. Data contains 5,000 files. You need to synchronize the file in the file share named data to an on-premises server named Server1. Which three actions should you perform? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point

Create a container instance
Register Server1
Install the Azure File Sync agent on Server1
Download an automation script
Create a sync group
Azure File Sync allows you to synchronize Azure file shares with Windows servers, enabling seamless hybrid cloud storage solutions. To synchronize the file share “data” on Store1 with Server1, follow these steps: Step 1: Install the Azure File Sync agent on Server1 The Azure File Sync agent is required on any on-premises Windows Server that will sync with an Azure file share. It enables communication between the local server and Azure File Sync. Step 2: Register Server1 with Azure File Sync After installing the agent, Server1 must be registered with Azure File Sync to be linked with the Azure Storage Account (Store1). This step ensures that the on-prem server is recognized and managed by Azure. Step 3: Create a Sync Group A Sync Group is used to establish the synchronization relationship between the Azure file share (Data on Store1) and the on-premises server (Server1). The cloud endpoint (Azure file share) and the server endpoint (a folder on Server1) are defined in this Sync Group. Why Other Options Are Incorrect: (a) Create a container instance ? Incorrect: Azure Container Instances (ACI) are used for running containers, not for file synchronization. (d) Download an automation script ? Incorrect: Automation scripts are not needed for setting up Azure File Sync. The process is done through the Azure Portal or PowerShell.
You have the Azure management groups shown in the following table: For each of the following statements, select the correct answers:
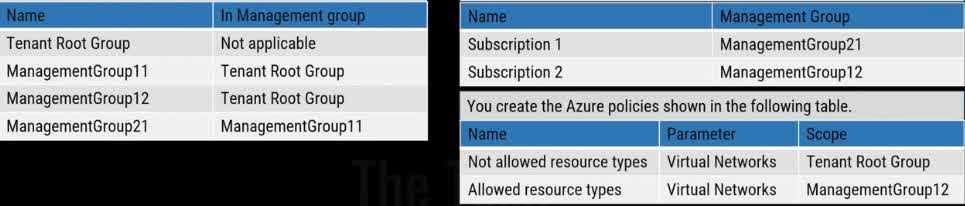
You can create a virtual network in subscription 1
You can create a virtual network in subscription 2
You can add subscription 1 to ManagementGroup11
Understanding the Management Group Hierarchy Tenant Root Group ManagementGroup11 ManagementGroup21 Subscription1 ManagementGroup12 Subscription2 Evaluating the Statements You can create a virtual network in Subscription1 False ? Since Subscription1 is under ManagementGroup21, which falls under ManagementGroup11, the “Not Allowed Resource Types: Virtual Networks” policy from the Tenant Root Group prevents virtual network creation. There is no exception policy allowing virtual networks in Subscription1. You can create a virtual network in Subscription2 True ? Even though the Tenant Root Group restricts virtual networks, ManagementGroup12 has an “Allowed Resource Types: Virtual Networks” policy that overrides the root policy for subscriptions under it. Since Subscription2 is under ManagementGroup12, virtual networks can be created. You can add Subscription1 to ManagementGroup11 True ? Subscription1 is already part of ManagementGroup21, which is under ManagementGroup11. There are no policy restrictions preventing Subscription1 from being moved directly under ManagementGroup11.
You have an Azure subscription that contains two virtual machines named VM1 and VM2. You create an Azure load balancer. You plan to create a load balancing rule that will load balance HTTPS traffic between VM1 and VM2. Which two additional load balancer resources should you create before you can create the load balancing rule?
a frontend IP address
a health probe
an inbound NAT rule
a virtual network
backend pool
Why “Health Probe” and “Backend Pool” Are Required Understanding the Scenario You have two virtual machines (VM1 and VM2). You created an Azure Load Balancer. You want to load balance HTTPS traffic (port 443) between VM1 and VM2. Before creating the load balancing rule, you must configure essential components. Required Components for a Load Balancing Rule To create a load balancing rule, you need two additional resources: Backend Pool ? A backend pool contains the virtual machines (VM1 and VM2) that will receive traffic from the load balancer. Without a backend pool, the load balancer won’t know which VMs to forward traffic to. Health Probe ? A health probe continuously checks the status of VM1 and VM2. If one of the VMs is down (e.g., unresponsive to HTTPS requests), the load balancer stops sending traffic to that VM. This ensures that users are only routed to healthy virtual machines.
You plan to use the Azure Import/Export service to copy files to a storage account. Which two files should you create before you prepare the drives for the import job?
an XML manifest file
a dataset CSV file
a JSON configuration file
a PowerShell PST file
a driveset CSV file
Why “Dataset CSV File” and “Driveset CSV File” Are Required The Azure Import/Export service allows you to securely transfer large amounts of data to an Azure Storage account by shipping physical hard drives to a Microsoft data center. Before preparing the drives for an import job, you need to create two important files: 1. Dataset CSV File ? The dataset CSV file specifies which files and folders should be copied from the drive to the Azure Storage account. It acts as a blueprint for the import job, ensuring that the correct files are uploaded. The file includes details like: Source path of the files Destination in Azure Storage File sizes Metadata (e.g., timestamps, permissions, etc.) 2. Driveset CSV File ? The driveset CSV file contains details about the physical drives being used for the import job. It ensures that Microsoft can properly process the incoming drives and match them to the correct import job. The file includes: Drive Serial Numbers BitLocker Encryption Keys (if applicable) Job Name and Storage Account Details Why Not the Other Options? XML Manifest File is not used in Azure Import/Export jobs. JSON Configuration File is not a required format for configuring these jobs. PowerShell PST File is not relevant to the Import/Export process.
You have a Microsoft 365 tenant and an Azure Active Directory (Azure AD) tenant named contoso.com. You plan to grant three users named User1, User2, and User3 access to a temporary Microsoft SharePoint document library named Library1.You need to create groups for the users. The solution must ensure that the groups are deleted automatically after 180 days. Which two groups should you create? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
an Office 365 group that uses the Assigned membership type
a Security group that uses the Assigned membership type
an Office 365 group that uses the Dynamic User membership type
Security group that uses the Dynamic User membership type
a Security group that uses the Dynamic Device membership type
The requirement is to grant access to a temporary Microsoft SharePoint document library while ensuring that the groups are automatically deleted after 180 days. In Azure AD, group expiration policies apply only to Office 365 (Microsoft 365) groups, not to security groups. This means that to ensure the groups are automatically deleted after a certain period, Office 365 groups must be used. Why These Two Answers? ? Office 365 Group with Assigned Membership (Option A) You manually assign specific users (User1, User2, User3) to the group. Ensures direct control over who has access. Can be used for collaboration tools like SharePoint, Teams, Outlook, and Planner. Subject to group expiration policies, allowing it to be deleted automatically after 180 days. ? Office 365 Group with Dynamic User Membership (Option C) Users are automatically added/removed based on rules (e.g., department, role, or attributes). Eliminates the need for manual management of users. Also supports group expiration policies, ensuring automatic deletion after 180 days. Why Not the Other Options? ? (b) Security group with Assigned Membership Security groups are used for access control (not collaboration). Security groups do not support expiration policies, so they will not be automatically deleted after 180 days. ? (d) Security group with Dynamic User Membership Same issue as (b) — security groups do not expire automatically. While dynamic membership helps automate user management, it does not meet the requirement for automatic deletion. ? (e) Security group with Dynamic Device Membership This is meant for devices, not users. Irrelevant for granting access to a SharePoint document library.
Which two of the following are elements of Template schema?
includes
parameters
scripts
outputs
In Azure Resource Manager (ARM) templates, the template schema consists of various elements that define how resources are deployed in Azure. Two key elements of this schema are parameters and outputs. Parameters Definition: Parameters allow you to pass dynamic values into an ARM template at deployment time instead of hardcoding values. Purpose: This makes templates reusable and customizable. Outputs Definition: Outputs return information about deployed resources after the template execution is complete. Purpose: Helps in retrieving resource properties, connection strings, or any values required after deployment. Why Other Options Are Incorrect? includes ? There is no includes section in an ARM template schema. scripts ? ARM templates do not have a scripts section. Instead, scripting is handled using deployment extensions or Azure PowerShell/CLI.
You have an Azure subscription that contains multiple virtual machines in the West US Azure region. You need to use Traffic Analytics in Azure Network Watcher to monitor virtual machine traffic. Which two resources should you create? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
a Data Collection Rule (OCR) in Azure Monitor
a Log Analytics workspace
an Azure Monitor workbook
a storage account
A Network watcher-enabled subscription
To use Traffic Analytics in Azure Network Watcher, you need to ensure that network traffic data is collected and analyzed properly. This requires two key resources: 1?? A Log Analytics Workspace 2?? A Network Watcher Enabled Subscription Why These Are the Correct Answers? ? 1. A Log Analytics Workspace (LAW) – Required for Data Storage and Analysis Traffic Analytics collects network flow logs and stores them in a Log Analytics workspace in Azure Monitor. The workspace is used to query, analyze, and visualize network traffic data using Kusto Query Language (KQL). Without a Log Analytics workspace, Traffic Analytics cannot store or process network traffic data. ? 2. A Network Watcher Enabled Subscription – Required for Traffic Monitoring Network Watcher is an Azure service that provides network monitoring, diagnostics, and analytics. It must be enabled in the Azure subscription and region where the virtual machines (VMs) are deployed. Without Network Watcher, Traffic Analytics cannot collect traffic flow logs from NSGs (Network Security Groups). Why Not the Other Options? ? a) A Data Collection Rule (DCR) in Azure Monitor DCRs are used for custom data collection in Azure Monitor but are not required for Traffic Analytics. Traffic Analytics relies on NSG Flow Logs and Log Analytics workspaces instead of DCRs. ? c) An Azure Monitor Workbook Workbooks only visualize data from Log Analytics but do not enable traffic monitoring. While useful for reports, they are not required to enable Traffic Analytics. ? d) A Storage Account NSG Flow Logs can be stored in a Storage Account, but Traffic Analytics requires Log Analytics for processing. While a Storage Account can be used for raw logs, it is not necessary for Traffic Analytics to function.
You have an Azure subscription. Users access the resources in the subscription from either home or from customer sites. From home, users must establish a point-to-site VPN to access the Azure resources. The users on the customer sites access the Azure resources by using site-to-site VPNs. You have a line-of-business app named App1 that runs on several Azure virtual machines. The virtual machines run Windows Server 2016. You need to ensure that the connections to App1 are spread across all the virtual machines. What are two possible Azure services that you can use? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
an internal load balancer
a public load balancer
an Azure Content Delivery Network (CDN)
Traffic Manager
an Azure Application Gateway
Your requirement is to ensure that connections to App1 are distributed across multiple virtual machines running in Azure. Since the users connect via Point-to-Site (P2S) VPN and Site-to-Site (S2S) VPN, their connections are private (not from the public internet). To properly distribute traffic among the Azure VMs running App1, the following services can be used: 1?? An Internal Load Balancer (ILB) 2?? An Azure Application Gateway Why These Are the Correct Answers? ? 1. Internal Load Balancer (ILB) – Balances Private Traffic Since users connect via VPN (P2S & S2S), the traffic is internal and private, meaning it does not come from the public internet. An Internal Load Balancer (ILB) distributes traffic only within an Azure virtual network (VNet). It ensures that requests from VPN users are evenly distributed among all the VMs running App1. Since this is a Line-of-Business (LoB) application used internally, an internal load balancer is the best fit. ? 2. Azure Application Gateway – Provides Load Balancing for Web Applications If App1 is a web application (HTTP/HTTPS-based), then Azure Application Gateway is a great solution. It provides Layer 7 (Application Layer) load balancing, supporting features like: URL-based routing SSL termination Web Application Firewall (WAF) for security It ensures that incoming requests from VPN users are evenly distributed across the VMs running App1. Why Not the Other Options? ? b) A Public Load Balancer – Incorrect A Public Load Balancer is used for distributing internet-facing traffic (from public IPs). App1 is accessed privately over VPN, so a public load balancer would not work in this scenario. ? c) Azure Content Delivery Network (CDN) – Incorrect Azure CDN is used for caching static content (images, videos, web pages) at global edge locations. It does not distribute traffic to virtual machines, so it does not help balance requests to App1. ? d) Traffic Manager – Incorrect Traffic Manager is a DNS-based traffic distribution service that directs users to the best Azure region. It works at the DNS level, not at the VM or network level. Since all users are already connected to a specific Azure VNet via VPN, Traffic Manager is unnecessary.
You have an Azure virtual machine named VM1 and an Azure key vault named Vault1. On VM1, you plan to configure Azure Disk Encryption to use a key encryption key (KEK). You need to prepare Vault for Azure Disk Encryption. Which two actions should you perform on Vault1? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
Create a new key
Select Azure Virtual machines for deployment
Configure a key rotation policy
Create a new secret
Select Azure Disk Encryption for volume encryption
Azure Disk Encryption (ADE) helps encrypt virtual machine (VM) disks using Azure Key Vault (AKV) for managing encryption keys. When using Key Encryption Key (KEK), you must prepare Azure Key Vault to store and manage the keys. Required Steps to Prepare Vault1 for Azure Disk Encryption 1?? Create a new key ? Why? Azure Disk Encryption requires a Key Encryption Key (KEK) to encrypt and protect the disk encryption keys. You must manually create or import a key into Azure Key Vault before configuring encryption on VM1. This key is used to encrypt the BitLocker encryption key for Windows VMs or the dm-crypt passphrase for Linux VMs. 2?? Configure a key rotation policy ? Why? Key rotation ensures automatic periodic renewal of encryption keys to enhance security. Azure Disk Encryption can be configured to use updated keys automatically, reducing risk in case of compromised keys. ? Why Not the Other Options? ? b) Select Azure Virtual Machines for deployment – Incorrect This option is related to deploying secrets to VMs but is not required to set up Azure Disk Encryption. ? d) Create a new secret – Incorrect Secrets in Azure Key Vault are typically used for passwords, connection strings, and certificates, not for encryption keys. ADE requires a Key Encryption Key (KEK), which is stored as a key, not a secret. ? e) Select Azure Disk Encryption for volume encryption – Incorrect While Azure Disk Encryption needs to be enabled for VM1, this setting is applied at the VM level, not in Key Vault. The Key Vault preparation step focuses on creating and managing encryption keys, not enabling ADE directly.
You are configuring Azure Active Directory (Azure AD) authentication for an Azure Storage account named storage1. You need to ensure that the members of a group named Group1 can upload files by using the Azure portal. The solution must use the principle of least privilege. Which two roles should you configure for storage1? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point
Storage Account Contributor
Storage Blob Data Contributor
Contributor
Reader
Storage Blob Data Reader
To ensure that members of Group1 can upload files to storage1 using Azure AD authentication while following the principle of least privilege, you need to assign the correct roles with the required permissions. 1. Required Permissions for Uploading Files in Azure Storage: To upload files in the Azure portal, users need: ? Access to the storage account and blob data ? Permissions to upload, delete, and manage blobs
You have downloaded an Azure Resource Manager (ARM) template to deploy numerous virtual machines (VMs). The ARM template is based on a current VM but must be adapted to reference an administrative password. You need to make sure that the password cannot be stored in plain text. You are preparing to create the necessary components to achieve your goal. Which of the following should you create to achieve your goal?
Azure Key Vault
Azure Storage account
Azure Active Directory(AD)
identity protections
Azure Access policy
Azure Backup policy
When using an Azure Resource Manager (ARM) template to deploy virtual machines (VMs), storing the administrative password in plain text is a security risk. Instead, the password should be securely stored and retrieved during deployment. Azure Key Vault is the best solution for securely managing passwords, secrets, and certificates. How Azure Key Vault and Azure Access Policy help? 1. Azure Key Vault Purpose: Securely stores sensitive information like passwords, certificates, and API keys. Why needed? The ARM template can reference the password stored in Azure Key Vault, ensuring it is never exposed in plain text. How it works? The password is stored as a secret in Key Vault. The ARM template uses a reference to retrieve the secret at deployment time instead of embedding the password. 2. Azure Access Policy Purpose: Controls who and what can access secrets stored in Azure Key Vault. Why needed? The ARM template (or the identity running the deployment) needs permissions to retrieve the secret from Key Vault. An Azure Access Policy must be configured to allow the necessary read access to the Key Vault secret for the VM deployment process.
