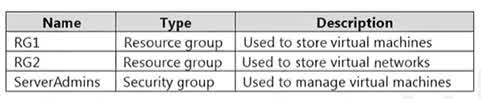
Question#QUE1511: You have an Azure subscription that contains the resources shown in the following table. see the image1 You need to ensure that ServerAdmins can perform the following tasks: Create virtual machines in RG1 only. Connect the virtual machines to the existing virtual networks in RG2 only. The solution must use the principle of least privilege. Which two role-based access control (RBAC) roles should you assign to ServerAdmins? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
a custom RBAC role for RG2
the Network Contributor role for RG2
the Contributor role for the subscription
a custom RBAC role for the subscription
the Network Contributor role for RG1
the Virtual Machine Contributor role for RG1
To meet the requirements using the principle of least privilege, you need to assign two specific roles: For creating virtual machines in RG1: Assigning the Virtual Machine Contributor role for RG1 (Option F) to the ServerAdmins group is the most specific, least-privileged role. It allows them to create and manage VMs but only within the scope of the RG1 resource group. For connecting VMs to networks in RG2: The ServerAdmins group needs permission to join a network interface to a virtual network in RG2 (Microsoft.Network/virtualNetworks/subnets/join/action). The built-in Network Contributor role (Option B) is too permissive as it also allows creating and deleting networks. Therefore, creating a custom RBAC role for RG2 (Option A) with only the required join permission is the most appropriate, least-privileged solution.
Question#QUE1466: You have an Azure subscription that contains 100 virtual machines and has Azure Security Center Standard tier enabled. You plan to perform a vulnerability scan of each virtual machine. You need to deploy the vulnerability scanner extension to the virtual machines by using an Azure Resource Manager template. Which two values should you specify in the code to automate the deployment of the extension to the virtual machines? Each correct answer presents part of the solution.
the user-assigned managed identity
the workspace ID
the Azure Active Directory (Microsoft Entra ID) ID
the Key Vault managed storage account key
the system-assigned managed identity
the primary shared key
To automate the deployment of the vulnerability scanner extension using an ARM template, you need to specify the user-assigned managed identity and the Azure Active Directory (Microsoft Entra ID) ID in the template. These values are necessary for the extension to authenticate and operate correctly within your Azure environment.
Question#QUE1455: You have an Azure subscription that contains a user named User1 and an Azure Container Registry named ConReg1. You enable content trust for ContReg1. You need to ensure that User1 can create trusted images in ContReg1. The solution must use the principle of least privilege. Which two roles should you assign to User1? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
AcrQuarantineReader
Contributor
AcrPush
AcrImageSigner
AcrQuarantineWriter
To create trusted images in an Azure Container Registry with content trust enabled, a user needs two specific permissions: AcrPush: This role is required to push new images to the registry. AcrImageSigner: This role is required to sign the pushed images, which is a necessary step for content trust. Assigning both roles to User1 meets the requirements while adhering to the principle of least privilege.
Question#QUE1432: You have an Azure subscription linked to a Microsoft Entra ID tenant named contoso.com. Contoso.com contains a user named User1 and an Azure web app named App1. You plan to enable User1 to perform the following tasks: Configure contoso.com to use Microsoft Entra Verified ID. Register App1 in contoso.com. You need to identify which roles to assign to User1. The solution must use the principle of least privilege. Which two roles should you identify? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
Authentication Policy Administrator
Authentication Administrator
Cloud App Security Administrator
Application Administrator
User Administrator
To configure your tenant for Microsoft Entra Verified ID, you need the global administrator or the authentication policy administrator permission for the directory you want to configure. For app registration, you need the application administrator permission. If you’re not the global administrator, you need both the authentication policy administrator and application administrator permissions to complete the required tasks.
Question#QUE1428: You have an Azure subscription that contains a web app named App1. Users must be able to select between a Google identity or a Microsoft identity when authenticating to App1. You need to add Google as an identity provider in Microsoft Entra ID. Which two pieces of information should you configure? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
a client ID
a tenant name
the endpoint URL of an application
a tenant ID
a client secret
To configure Google federation in Microsoft Entra ID, you need the Google client ID and client secret. You can use the Azure portal or PowerShell to configure this. Steps include: Sign in to the Azure portal as an External Identity Provider Administrator or a Global Administrator. In the left pane, select Azure Active Directory. Select External Identities. Select All identity providers, then select the Google button. Enter the client ID and client secret you obtained earlier, then select Save.
Question#QUE1419: Your network contains an Active Directory forest named contoso.com. You have an Azure Directory (Microsoft Entra ID) tenant named contoso.com. You plan to configure synchronization by using the Express Settings installation option in Microsoft Entra ID Connect. You need to identify which roles and groups are required to perform the planned configurations. The solution must use the principle of least privilege. Which two roles and groups should you identify? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
the Domain Admins group in Active Directory
the Security administrator role in Microsoft Entra ID
the Global administrator role in Microsoft Entra ID
the User administrator role in Microsoft Entra ID
the Enterprise Admins group in Active Directory
To configure synchronization using Express Settings in Microsoft Entra ID Connect, you need the Global administrator role in Microsoft Entra ID and membership in the Enterprise Admins group in Active Directory.
Question#QUE1416: You have an Azure subscription. You create an Azure web app named Contoso1812 that uses an S1 App service plan. You create a DNS record for www.contoso.com that points to the IP address of Contoso1812. You need to ensure that users can access Contoso1812 by using the https://www.contoso.com URL. Which two actions should you perform? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
Turn on the system-assigned managed identity for Contoso1812.
Add a hostname to Contoso1812.
Scale out the App Service plan of Contoso1812.
Add a deployment slot to Contoso1812.
Scale up the App Service plan of Contoso1812.
Upload a PFX file to Contoso1812.
To enable access to the web app using a custom domain and HTTPS, you must add the custom hostname to the web app and upload a PFX certificate file for SSL binding.
Question#QUE1406: Your company has an Azure subscription that includes two virtual machines, named VirMac1 and VirMac2, which both have a status of Stopped (Deallocated). The virtual machines belong to different resource groups, named ResGroup1 and ResGroup2. You have also created two Azure policies that are both configured with the virtualMachines resource type. The policy configured for ResGroup1 has a policy definition of Not allowed resource types, while the policy configured for ResGroup2 has a policy definition of Allowed resource types. You then create a Read-only resource lock on VirMac1, as well as a Read-only resource lock on ResGroup2. Which of the following is TRUE with regards to the scenario? (Choose all that apply.)
You will be able to start VirMac1.
You will NOT be able to start VirMac1.
You will be able to create a virtual machine in ResGroup2.
You will NOT be able to create a virtual machine in ResGroup2.
A Read-only lock on VirMac1 prevents starting the VM, so you will NOT be able to start VirMac1. A Read-only lock on ResGroup2 does not prevent creating new resources, so you will be able to create a virtual machine in ResGroup2.
Question#QUE1398: Which of these roles are able to make changes to the default security policy in Microsoft Defender for Cloud? (Choose 2 answers).
End User
Contributor
Subscriber
Owner
The ability to make changes to the default security policy requires you to be an owner, contributor, or a security administrator of the Azure subscription.
Question#QUE1389: You are configuring security settings for your Azure Data Lake, and want to integrate a Data Lake service endpoint within an existing VNet. Which steps should you implement to configure this? (Choose 2 answers)
Configure your Azure Data Lake in the same resource group as your VNet
Configure a Microsoft Azure Active Directory Service endpoint
Deploy the endpoint in your selected VNET
Disable connectivity from Azure services outside of the selected VNET
To use virtual network integration with data lake storage gen1, you must create a virtual network in the same region as your data lake storage account. You need to configure a service endpoint with the Microsoft Azure Active Directory as the service. After creating your virtual network in the same region as your data lake, you need to go to your data lake and click on Firewall and virtual networks. Choose the Selected network radio button and then Add existing virtual network. In the Add networks blade, select your virtual network and the subnet and click Add. Below the firewall section under exceptions, you can enable connectivity from Azure services outside of your selected network.
Question#QUE1381: You have an Azure Container Registry named Registry1. From Azure Security Center, you enable Azure Container Registry vulnerability scanning of the images in Registry1. You perform the following actions: Push a Windows image named Image1 to Registry1. Push a Linux image named Image2 to Registry1. Push a Windows image named Image3 to Registry1. Modify Image1 and push the new image as Image4 to Registry1. Modify Image2 and push the new image as Image5 to Registry1. Which two images will be scanned for vulnerabilities? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
Image4
Image2
Image1
Image3
Image5
Only Linux images are scanned for vulnerabilities in Azure Container Registry. Windows images are not scanned.
Question#QUE1368: You have an Azure subscription that contains a user named User1 and an Azure Container Registry named ContReg1. You enable content trust for ContReg1. You need to ensure that User1 can create trusted images in ContReg1. The solution must use the principle of least privilege. Which two roles should you assign to User1? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
AcrQuarantineReader
Contributor
AcrPush
AcrImageSigner
AcrQuarantineWriter
To create trusted images in an Azure Container Registry with content trust enabled, User1 needs the AcrPush role (to push images) and the AcrImageSigner role (to sign images as trusted). This follows the principle of least privilege.
Question#QUE1340: You want to gather logs from a large number of Windows Server 2016 computers using Azure Log Analytics. You are configuring an Azure Resource Manager template to deploy the Microsoft Monitoring Agent to all the servers automatically. Which of the following should be included in the template? (Choose all that apply.)
WorkspaceID
Microsoft Entra IDApplicationID
WorkspaceKey
StorageAccountKey
To configure the Microsoft Monitoring Agent to connect to Azure Log Analytics, you need to provide the WorkspaceID and WorkspaceKey in the template. These values allow the agent to authenticate and send data to the correct Log Analytics workspace. Microsoft Entra IDApplicationID and StorageAccountKey are not required for this configuration.
Question#QUE1333: You have an Azure subscription. You configure the subscription to use a different Azure Active Directory (Microsoft Entra ID) tenant. What are two possible effects of the change? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
Role assignments at the subscription level are lost.
Virtual machine managed identities are lost.
Virtual machine disk snapshots are lost.
Existing Azure resources are deleted.
When you change the Azure Active Directory (Microsoft Entra ID) tenant associated with a subscription: Role assignments at the subscription level are lost because they are tied to the original directory. Virtual machine managed identities are lost because managed identities are also linked to the original directory. Virtual machine disk snapshots and existing Azure resources are not deleted or lost as a result of changing the directory.
Question#QUE1327: Your network contains an Active Directory forest named contoso.com. You have an Azure Active Directory (Microsoft Entra ID) tenant named contoso.com. You plan to configure synchronization by using the Express Settings installation option in Microsoft Entra ID Connect. You need to identify which roles and groups are required to perform the planned configuration. The solution must use the principle of least privilege. Which two roles and groups should you identify? Each correct answer presents part of the solution.
the Domain Admins group in Active Directory
the Security administrator role in Microsoft Entra ID
the Global administrator role in Microsoft Entra IDthe Global administrator role in Microsoft Entra ID
the User administrator role in Microsoft Entra ID
the Enterprise Admins group in Active Directory
To configure synchronization using Microsoft Entra ID Connect (Azure AD Connect) with Express Settings, you need: Enterprise Admins group in Active Directory: This group has the necessary permissions to create and configure objects in the on-premises Active Directory forest. Global administrator role in Microsoft Entra ID: This role is required to grant the necessary permissions in Azure AD for directory synchronization. These roles and groups provide the required permissions for the setup while following the principle of least privilege.
Color of Sky?

Blue
Black
Red

Sky color is blue due to refraction

Question#QUE1318: You have deployed multiple AKS nodes with a Linux operating system and as a security best practice, you want to regularly review and update security settings for the operating system. Which statements below describe how security patches are applied to AKS nodes with a Linux operating system? (Choose 2 answers)
All node operating systems are automatically upgraded nightly.
AKS automatically applies the latest updates.
AKS automatically reboots nodes as required to complete an update.
AKS automatically performs node pool upgrades nightly.
For Linux nodes in AKS, Azure automatically applies the latest OS security patches on a nightly basis. This ensures that the nodes are kept up to date with the latest security updates. However, if a Linux OS update requires a host reboot, that reboot is not performed automatically. Instead, you must manually reboot the node when convenient, or use a tool like Kured (an open-source reboot daemon for Kubernetes) to automate reboots. Node pool upgrades are not performed automatically nightly.
Question#QUE1316: You have been tasked with creating an Azure key vault using PowerShell. You have been informed that objects deleted from the key vault must be kept for a set period of 90 days. Which two of the following parameters must be used in conjunction to meet the requirement? (Choose two.)
EnabledForDeployment
EnablePurgeProtection
EnabledForTemplateDeployment
EnableSoftDelete
To ensure that deleted objects in Azure Key Vault are retained for a set period (such as 90 days), you must enable both Soft Delete and Purge Protection. EnableSoftDelete ensures that deleted objects are recoverable for a retention period (default is 90 days). EnablePurgeProtection prevents the permanent deletion (purge) of these objects during the retention period, enforcing the retention policy. Both settings together guarantee that deleted objects cannot be permanently removed until the retention period has expired.
Question#QUE1311: Your company uses Azure DevOps with branch policies configured. Which of the following is TRUE with regards to branch policies? (Choose all that apply.)
It enforces your team’s change management standards.
It controls who can read and update the code in a branch.
It enforces your team’s code quality.
It places a branch into a read-only state.
Branch policies in Azure DevOps help teams protect important branches of development by enforcing code quality and change management standards. They ensure that changes meet certain requirements (such as code reviews or successful builds) before being merged, but they do not control read/update permissions or make branches read-only.
Question#QUE1278: You have an Azure Active Directory (Microsoft Entra ID) tenant named contoso.com that contains a user named User1. You plan to publish several apps in the tenant. You need to ensure that User1 can grant admin consent for the published apps. Which two possible user roles can you assign to User1 to achieve this goal? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
Security administrator
Cloud application administrator
Application administrator
User administrator
Application developer
The Cloud application administrator and Application administrator roles both have permissions to manage applications in Azure AD, including granting admin consent to applications. This allows the user to approve permissions requested by applications on behalf of the organization. Other roles listed do not have the necessary permissions to grant admin consent for published apps.
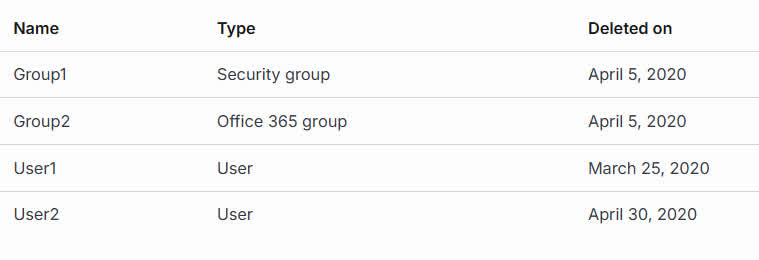
Question#QUE1276: You have an Azure Active Directory (Microsoft Entra ID) tenant. You have the deleted objects shown in the following table: On May 4, 2020, you attempt to restore the deleted objects by using the Azure Active Directory admin center. Which two objects can you restore? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
Group1
Group2
User2
User1
Deleted users and deleted Office 365 groups are available for restore for 30 days. You cannot restore a deleted security group.
Question#QUE1274: Your company has an Azure SQL database that has Always Encrypted enabled. You are required to make the relevant information available to application developers to allow them to access data in the database. Which two of the following options should be made available? Answer by select the correct Answers from the option
The column encryption key
A DLP policy
A shared access signature (SAS)
A key vault access policy
The column master key
Always Encrypted uses two types of keys: column encryption keys and column master keys. A column encryption key is used to encrypt data in an encrypted column. A column master key is a key-protecting key that encrypts one or more column encryption keys.
